Getting Started
This topic describes how to get started with Cisco XDR.
Once you subscribe to Cisco XDR, you will receive an email with a link to sign in to Security Cloud Control through Security Cloud Sign On. See Sign in to Security Cloud Control in the Getting Started Guide for New Customers of Security Cloud Control for more information on Security Cloud Sign On.
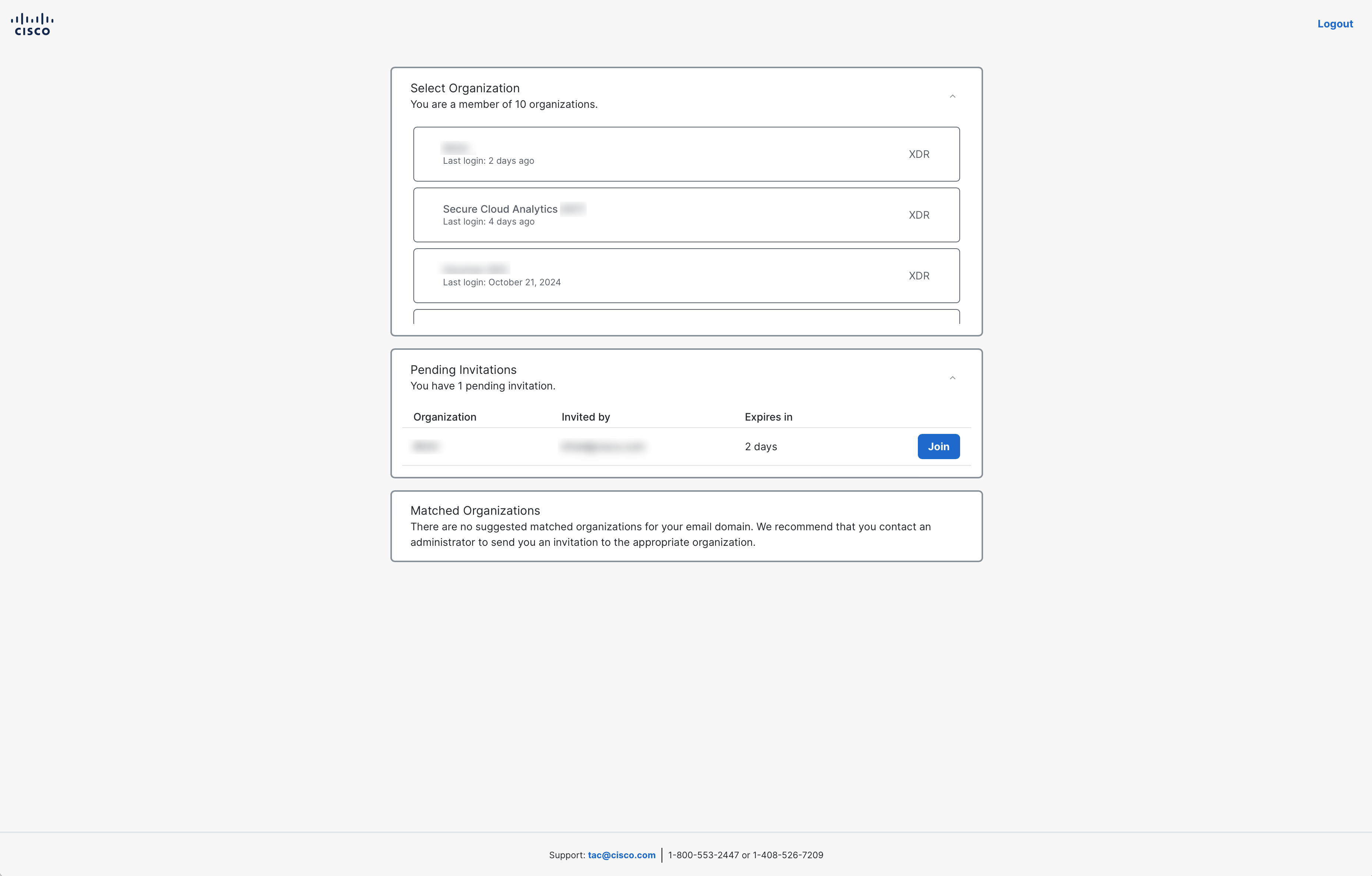
Once you sign in to Security Cloud Control, you must claim your subscription and activate Cisco XDR. For details, see Claim Your Product Subscriptions in the Getting Started Guide for New Customers of Security Cloud Control. After the product is activated, you can access Cisco XDR by clicking the nine-dot menu in the upper right corner and choose XDR. The following is displayed if you belong to multiple organizations.
-
Select Organization - If you are a member of two or more organizations, when you sign in to your Security Cloud Sign On account, a list of organizations is displayed in the Select Organization area. Click the organization card to log in to Cisco XDR for the selected organization. The date you last logged in to the organization and the application label (XDR) are also displayed. The XDR application label indicates that the current organization is a Cisco XDR organization.
-
Pending Invitations - A list of all your invitations to join an organization with a pending status is displayed, if applicable. Click Join to accept the pending invitation and join the organization. If your invitation expires, you can contact an Administrator for that organization to resend your invitation or request access to an organization in the Matched Organizations area.
-
Matched Organizations - A list of activated organizations that match the email domain provided is displayed, if applicable. Click Request Access to send an email to all the Administrators for that organization to approve your request to join the organization. The Request Access button changes to a Pending Access status.
-
Once the request is sent, all the Administrators for that organization will receive email requests to grant access to Cisco XDR or reject the access request.
-
If the request is rejected, the Pending Access status changes to Access Rejected and you will not have access to the organization. You can contact an Administrator for that organization to send you an invitation again in Cisco XDR.
-
If the request is expired, you can request access again or you can contact an Administrator for that organization to send you an invitation in Cisco XDR.
-
-
Logout - Click Logout in the upper right corner of the page to log out of the Security Cloud Sign On account.
If you are logged in with an Administrator role, you can invite users and manage user roles for Cisco XDR in Security Cloud Control. When you send an invitation to other users within your organization, you can assign an appropriate role to the user, depending on their role within your organization. For example, you can assign the Incident Responder role to a user who will be responsible for managing and resolving incoming incidents. For details, see Managing Role-Based Access Control in the Cisco Security Cloud Control Administration Guide.
If you have questions or need help, contact Cisco Support. For details, see Contact Support.
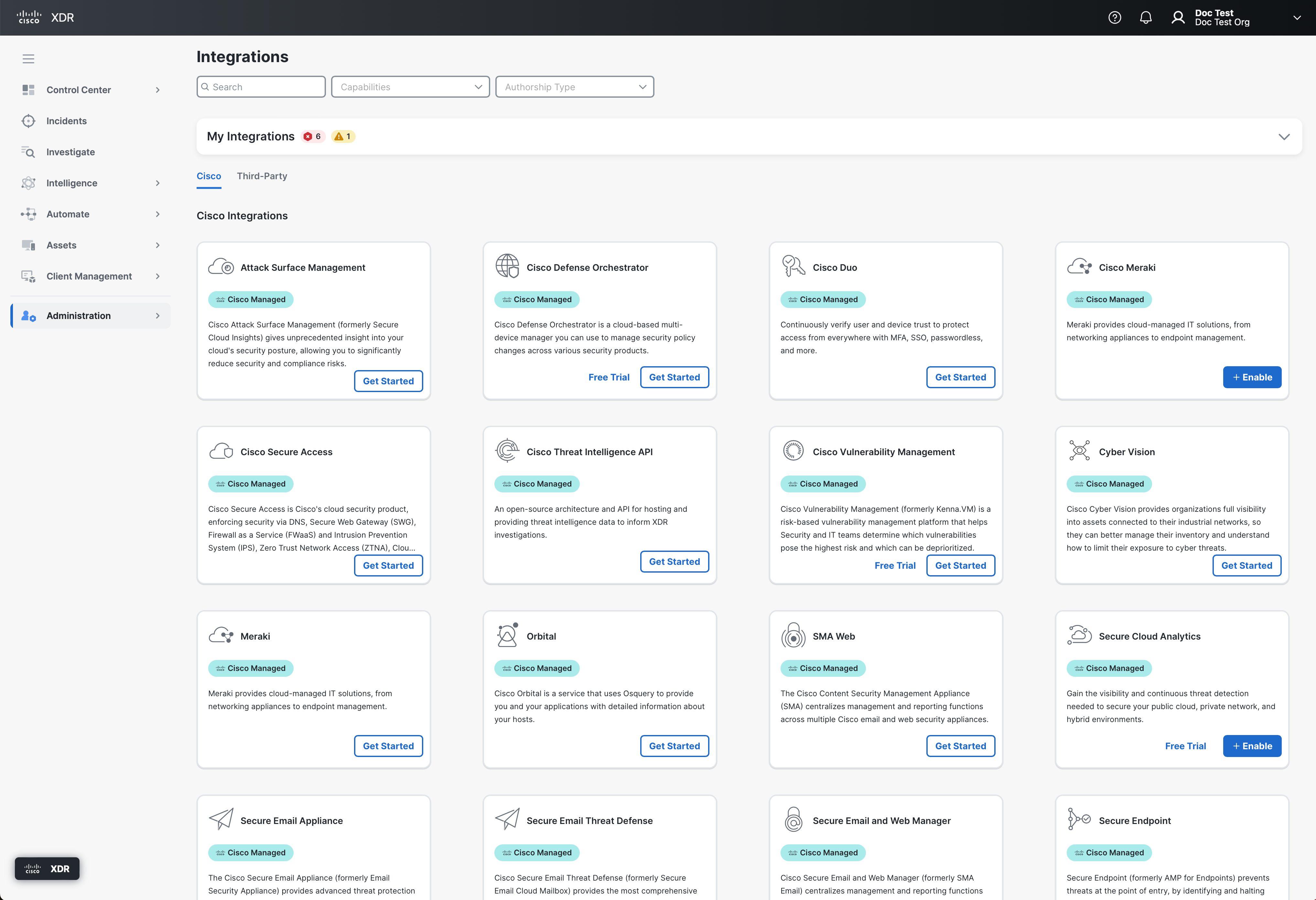
Cisco and third-party integrations allow you to generate incidents and make the most out of your Cisco XDR experience. We highly recommend that you integrate the following Cisco integrations:
-
Secure Endpoint
-
Secure Cloud Analytics
-
Umbrella
-
Cisco Duo
To learn more about the supported capabilities in Cisco XDR for Cisco and third-party integrations, see Cisco and Third-Party Integrations and Supported Capabilities. For details on how to add integrations, see Integrations.
Configure Integrations in Secure Cloud Analytics
Secure Cloud Analytics is now a part of Cisco XDR. You can configure the following integrations in Secure Cloud Analytics to collect telemetry for incident detection and correlation in Cisco XDR: Cisco Meraki, Cisco Umbrella, Cisco ISE, Cisco Attack Surface Management, Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Kubernetes.
For more information on configuring the Secure Cloud Analytics integrations, see Secure Cloud Analytics Documentation.
Cisco XDR includes the XDR Default Deployment, which can be installed on your endpoints to improve detections and enrich incidents. The XDR Default Deployment is associated with two default Secure Client profiles, Cloud Management Default Profile and NVM Cloud Default Profile, and is configured to send Network Visibility Module (NVM) cloud data to Cisco XDR.
Cisco XDR uses this data to create new detections, correlate multiple events into a single incident, and fill invisibility gaps in your network. For more information on installing the default deployment and viewing NVM data, see Default Deployments.
Cisco XDR Incidents is where security analysts and incident responders manage the incidents that have been promoted from security events. Through advanced analytics and correlation, Cisco XDR takes raw telemetry and uses detection logic to create meaningful security events which are shown as incidents.
The incidents are prioritized using an overall priority score calculated from detection risk (including incident severity and TTP-based risk of financial loss) and asset value at risk (based on the value of assets involved in the incident). This ensures that the most critical detections are surfaced at the top of the list, allowing your team to spend time on what really matters.
For more information, see Getting Started with Incident Response.
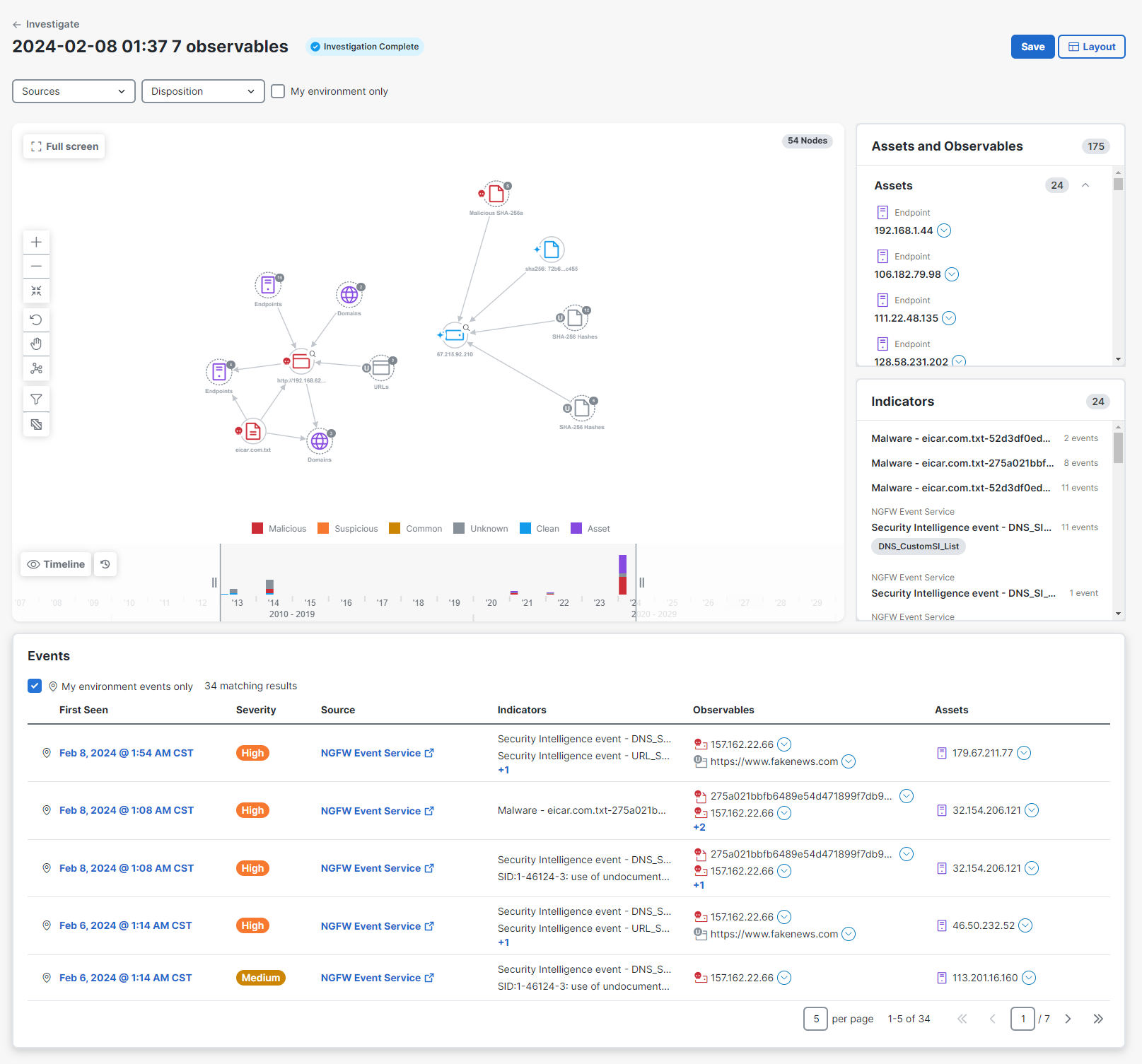
In an intelligence-driven incident response, a piece of disseminated information may be the starting point for a security team to investigate the impact of a known piece of malware. The Cisco XDR Investigate feature is used to search suspicious indicators of compromise (IOCs) such as emails, log messages, domains, URLs, and IPs, and extract observables for enrichment.
Cisco XDR reaches out to all of the configured sources (integrations) and finds the disposition for each observable, and then displays the details in the investigation results. Once an asset has been identified, you can immediately direct attention to it to gain contextual knowledge of exactly which observable(s) the asset has communicated with.
For more information, see Start an Investigation and Investigation Results.
The Cisco XDR Intelligence feature provides the ability to search for stored threat intelligence from the public, as well as your private, threat intelligence stores based on the Cisco Threat Intelligence Model. It includes the judgments, indicators, events, and feeds based on the data that has been extracted from the continuous enrichment of our threat intelligence sources and deemed most relevant to incident response.
For more information, see Intelligence.
Cisco XDR Automation enables you to import, create, and automate workflows that integrate various systems to save you time with repetitive tasks and accelerate investigation and response actions.
Pre-built activity blocks make building custom workflows easy. For information on creating workflows, see Workflows. For information on installing pre-built workflows, see Exchange.
Triggers cause a workflow to execute if certain criteria are met. Configure automation rules that determine when a workflow is executed, such as on a schedule or when an incident or specific event occurs. For more information, see Triggers.
The Response tab in the incident details page displays a playbook template to assist in building effective incident response plans, processes, and procedures. Execute workflows to automate some of the response tasks. For more information, see Initiate Incident Response.
The Cisco XDR Assets feature pulls data from integrated sources (for example, Secure Endpoint and Cisco Duo) to provide you with an inventory of devices and users in your organization. This comprehensive view provides you with the data and context you need to better identify vulnerabilities, prevent threats, and prioritize remediations.
The Dashboards page displays high-level metrics around your Security Operations Center. By default, the Overview dashboard is displayed for all users and it provides a high-level summary of the incidents within your organization, such as unassigned incidents and the mean time summary for your organization.
For details, see Dashboards.
-
Add your own dashboards from your Cisco integrations and you can share your dashboards with other users within your organization. For information on configuring and sharing custom dashboards, see Configure Dashboards and Cards.
-
Use the Cisco XDR ribbon to link incidents and observables to a case, find observables, view notifications, manage incidents, and run queries against your endpoints using the Orbital app. For more information, see Ribbon.
-
Install the Cisco XDR ribbon extension on your browser for all the same functionality as ribbon and to further extend the features in ribbon with the ability to accelerate response workflows and improve threat hunting directly from your browser by extracting observables from any web page or selected text on a page. For details, see Ribbon Extension.
-
Configure on-premises appliances to provide Cisco XDR permission to access an on-premises appliance. For details, see On-Premises Appliances.
-
Create API client credentials used to integrate your Cisco and third-party security products with Cisco XDR. For details, see API Clients.
-
Manage and customize incident response playbooks used by your organization and the rules used to assign them to incidents. For details, see Playbooks.
-
Create your own profiles and deployments in Client Management to control the Secure Client endpoint software. For details, see Client Management.
-
Create rules to assign values to devices to provide more context in Cisco XDR Incidents. For details, see Rules.
-
View and manage notifications that are sent to you if an incident or approval task is assigned to you by another user or if an Automation workflow or rule is temporarily disabled. For details, see Notifications.
-
View a coverage map of the MITRE ATT&CK® tactics and techniques that are covered by the Cisco and third-party products. For details, see MITRE ATT&CK® Coverage Map.
-
Acquire forensics data from assets and connect to assets using remote shell for remediation purposes. For details see XDR Forensics.