Integrations
Note: Only users with an Administrator role can add integrations.
With Cisco XDR, incident responders, threat hunters, and security analysts can better understand threats on their network by gathering, combining, and correlating local security observations (for example, EDR detections and network security alerts), networks and system telemetry (such as netflow data and system process details), and threat intelligence (such as Cisco Talos alerts about known threat actors). It brings together threat intelligence and local security context and control from multiple products all in one place for the security analyst. Each source of global or local intelligence is provided by an integration.
Cisco XDR offers integrations for Cisco security products and third-party solutions. The Integrations page allows you to configure and view your integrations, and to view all Cisco and third-party integrations that are available for configuration. For Cisco integrations, click Free Trial for information on how to try out the Cisco product, if available.
Integrated products are leveraged via their APIs. Authentication methods may vary per product but are typically API tokens or keys. Integrated products must be reachable from Cisco XDR's cloud infrastructure. For on-premises products, this can be accomplished via port forwarding, Automation Remote, or registering and configuring them as on-premises appliances.
Note: The threat intelligence and IT Service Management (ITSM) third-party integrations are included with the Cisco XDR Essentials licensing tier and all other third-party integrations require Cisco XDR Advantage or Cisco XDR Premier licensing tier. For details, see the Minimum Cisco XDR Licensing Tier Required column in Cisco and Third-Party Integrations and Supported Capabilities. If your organization's licensing tier is Cisco XDR Essentials, the threat intelligence and ITSM third-party integrations are available and a message is displayed at the top of the Third-Party tab with additional information on how to upgrade the license to access all third-party integrations and learn more about custom integrations. You can view your organization's licensing tier on the My Account page. For more information on the licensing tiers, see Cisco XDR Licenses.
Cisco Secure Cloud Analytics is now a part of Cisco XDR. You can configure the following integrations in Secure Cloud Analytics to collect telemetry for incident detection and correlation in Cisco XDR: Cisco Meraki, Cisco Umbrella, Cisco ISE, Cisco Attack Surface Management, Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Kubernetes. For more information on configuring the Secure Cloud Analytics integrations, see Secure Cloud Analytics Documentation.
The authorship type tag on the integration card, on the integration details page, and in the My Integrations panel indicates who created the integration.
-
Cisco Managed - Authored by Cisco and supported by Cisco Support.
-
Cisco Verified - Authored by a Cisco Security Technology Partner and supported by that partner.
The following table lists the IP addresses you must allow for Cisco XDR to access your product APIs:
|
Region |
Source IP Addresses |
|---|---|
| North America |
35.168.234.165, 35.172.5.95, 34.225.249.84, 18.213.248.192, 54.166.136.151, 54.211.175.37, 52.4.96.105, 52.44.231.95, 52.54.41.7, 52.55.87.127, 52.55.92.19, 52.205.26.61, 107.22.210.176, 107.22.217.211, 107.22.247.3 |
| Europe |
34.251.83.242, 52.49.85.99, 52.208.164.206, 3.251.20.134, 52.48.136.126, 63.33.97.243, 18.184.151.221, 18.184.220.206, 18.196.240.228, 18.184.238.96, 18.196.75.98, 52.58.161.32 |
|
Asia Pacific, Japan, and China |
54.248.49.240, 52.198.165.128, 52.196.126.178, 13.230.182.244, 18.181.14.110, 35.72.117.19, 3.105.113.178, 3.106.86.62, 13.236.79.226, 3.104.45.208, 13.210.255.103, 13.238.191.0 |
Prerequisite: If your product is an on-premises device, it must be registered in Security Services Exchange before adding the integration. See On-Premises Appliances.
-
Choose Administration > Integrations in the navigation menu.
You can filter the integrations that are displayed on the page based on capability. For details, see Filter Integrations. You can also search for integrations that are displayed on the page based on integration name and description. See Search Integrations for more information.
-
On the Integrations page, click the Cisco tab to view a list of Cisco integrations or the Third-Party tab to view a list of the third-party integrations.
-
Navigate to the integration you want to configure and click Get Started, Enable, or + in the integration card.
Note: If you click Enable, the configuration and activation of the integration is completed within the integrating product. Once enabled, it is automatically integrated in Cisco XDR and the integration is displayed under My Integrations. You do not need to complete the remaining steps.
-
Complete the form in the Add Integration area. For details on how to set up your integration, expand the Integration Guide panel by clicking the
 (Expand) icon and follow the instructions in the Integrations Guide panel.
(Expand) icon and follow the instructions in the Integrations Guide panel. -
Click Add to add the integration.
A health check is performed to determine if the integration was properly configured. Once the health check is completed, the status is displayed in the upper right corner indicating that either there were no issues with the configuration (Connected) or that errors were found (Error). If errors occurred, correct the configuration and click Add.
The integration is displayed in the My Integrations panel and the Status column shows whether it is Connected or if there is an Error with the configuration.
On the Integrations page, click the Capabilities or Authorship Type drop-down list and check the check boxes next to the capability or authorship type to filter the integrations that are displayed on the page.
The integrations that match your selections are displayed in the My Integrations panel, the Cisco tab, and the Third-Party tab. For more information on the capabilities, see Cisco and Third-Party Integrations and Supported Capabilities and for details on the authorship types, see Authorship Types.
Enter the search criteria in the Search field on the Integrations page to search for integrations by the integration name and description. The integrations that match your search criteria are displayed in the My Integrations panel, the Cisco tab, and the Third-Party tab.
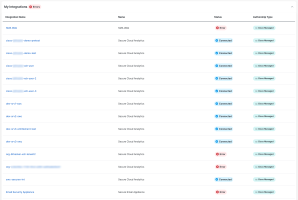
All integrations configured for your environment are shown in the My Integrations panel on the Integrations page. The total number of configuration errors found with all your integrations is displayed next to My Integrations and you can view the error messages by clicking the error tag.
Click the ![]() (Expand) icon to display all the configured integrations. The Status column indicates whether the module is Connected (successfully configured) or if it has an Error with the configuration. Click the error tag to view the error details.
(Expand) icon to display all the configured integrations. The Status column indicates whether the module is Connected (successfully configured) or if it has an Error with the configuration. Click the error tag to view the error details.
The Authorship Type column indicates who created the integration. For details, see Authorship Types.
All integrations configured for your environment are shown in the My Integrations drop-down area. The Status column whether the integration is Connected (successfully configured) or if it has an Error with the configuration. If it has errors, you can edit the integration:
-
Choose Administration > Integrations in the navigation menu and expand the My Integrations panel.
-
In the Integration Name column, click the row of the integration you want to edit. The Edit Integration area displays the current integration settings.
-
Edit the settings as needed, and click Save.
A health check is performed to determine if the integration was properly configured. A message is displayed in the upper portion of the page, indicating that the health check is running. Once it completes, a message displays indicating that either there were no issues with the configuration or that errors were found.
-
Choose Administration > Integrations in the navigation menu and expand the My Integrations panel.
-
In the Integration Name column, click the row of the integration you want to delete. The Edit Integration area displays the current integration settings.
-
Click Delete.
-
On the confirmation dialog, click Delete.
The integration is removed and its data is no longer available.
By default, the following integrations are automatically integrated with Cisco XDR:
- Cisco File Reputation - Cisco File Reputation is the database that powers Cisco file hash lookups. It stores billions of file hashes and associated dispositions, sourced from Cisco Talos, Cisco Secure Malware Analytics, and other trusted providers. By default, Cisco XDR comes configured to connect to Cisco File Reputation.
- Cisco XDR Global Threat Intelligence - The Cisco XDR Global Threat Intelligence is a repository of Cisco and third-party intelligence curated by Cisco. By default, Cisco XDR comes configured to connect to Cisco XDR Global Threat Intelligence.
- Private Intelligence - Private Intelligence is a data storage facility built into Cisco XDR to store the incidents that display in Cisco XDR Incidents list, casebooks, snapshots, and user-provided data used in investigations, such as the user’s own threat intelligence or internal observations by other security tools. By default, Cisco XDR comes configured to connect to Private Intelligence.
- Talos Intelligence - Talos is Cisco’s industry-leading threat intelligence team that protects your organization’s people, data and infrastructure from active adversaries. The Talos team collects information about existing and developing threats, and provides comprehensive protection against more attacks and malware than anyone else. All Cisco Security products utilize Talos threat intelligence, providing fast and effective security solutions. Their job is protecting your network.