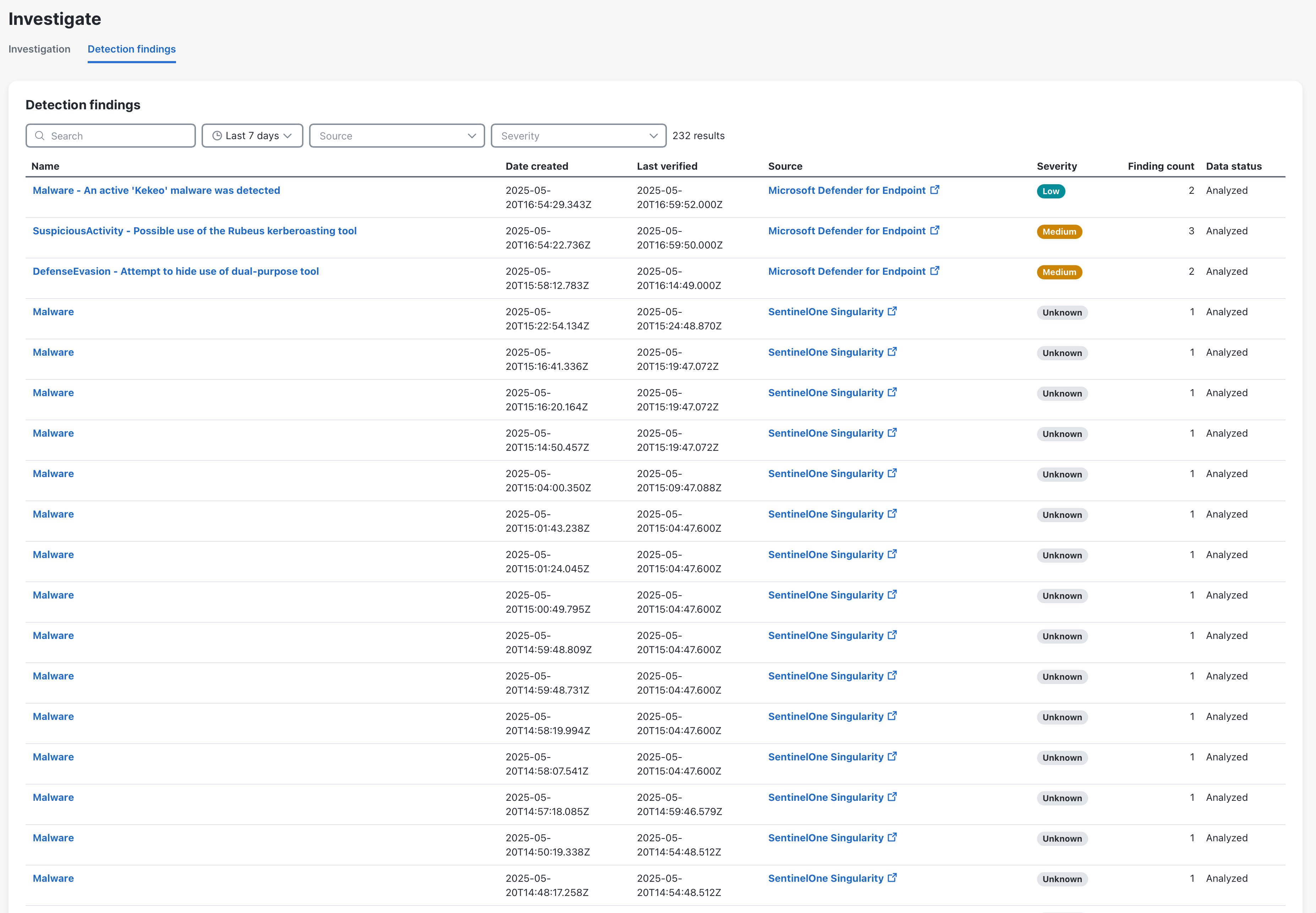
Detection Findings
The Detection findings tab displays all the security events generated by integrated products and the Cisco XDR native telemetry sent from the following sources: Network, Cloud, Identity, and Endpoint. The security events allow you to validate the data that is ingested by Cisco XDR for incident correlation. For details on how the security events are grouped and enriched by the correlation engine in Cisco XDR to create incidents in Cisco XDR, see Detection. You can also create custom security events using the Findings Intake API. For more information, see Cisco Developer - Cisco XDR API Documentation.
The following is a list of supported Cisco and third-party products that generate security events if integrated in Cisco XDR:
The Cisco and third-party integrations are configured on the Integrations page. For details on adding an integration, see Integrations.
The Cisco XDR source refers to the Cisco XDR native telemetry sent from endpoint and the following sources that are integrated in Cisco Secure Cloud Analytics: network, cloud, and identity. For more information, see Cisco Secure Cloud Analytics. The Network Visibility Module data is sent to Cisco XDR from the endpoint source if you install the default deployment on your endpoints. For more information on installing the default deployment and viewing endpoints data, see Default Deployments.
You can filter the types of security events to narrow the list of results in the table.
Choose Investigate > Detection Findings in the navigation menu to view the security events from Cisco XDR native sources and integrated products.
Note: The detection findings table displays the first 10,000 security events only.
|
Column Name |
Description |
|---|---|
|
Name |
Name of the security event. |
|
Date created |
Date and time the security event was created by the source. |
|
Last verified |
Date and time the security event was last processed by Cisco XDR. |
|
Source |
Name of the integrated product that generated the security event. Click the source link to open the security event in the integrated product. |
|
Severity |
Threat level of the security event (Critical, High, Medium, Low, Informational, Unknown). |
| Finding count | Number of detection findings derived from the security event. |
| Data status | Status of whether the security event has been analyzed by Cisco XDR for incident correlation. |
|
Related incidents |
Displays all the current incidents that contain the security event. The em dash (—) is displayed if there are no incidents associated with the security event. Click the incident link to open the incident detail in a new tab. For more information on incidents, see Incidents. |
|
Source details |
Instance name provided by the user when configuring the integrated product that generated the security event. This is an optional column that is only available in the Table settings drawer. For details, see Customize Columns. |
You can search and filter the security events to narrow the display to only those security events you want to view.
Use the Search field in the upper portion of the page to narrow down the display of security events. The search is triggered as you enter the criteria. You can search for security events by partial or complete name. Search entries are not case sensitive.
The security events that are displayed in the list are those that have been created within the specified date range, subject to your data retention policy. By default, the list includes security events created within the last 7 days. You can narrow the display of security events based on a specific timeframe using the date created drop-down menu above the security events list.
Click the date created drop-down list and choose the date range for the security events you want to display:
-
Last 24 hours - Displays security events created within the last 24 hours that match the filter criteria.
-
Last 7 days - Displays security events created within the last 7 days that match the filter criteria.
-
Last 30 days - Displays security events created within the last 30 days that match the filter criteria.
-
Last year - Displays security events created within the last year that match the filter criteria.
-
Custom range - Displays security events created within the specified start and end date, and that match the filter criteria.
The date range selected is displayed in the Applied Filters area. Click the ![]() (Expand) icon to display all the filter selections with the filter category and the filter tags. To remove a selected filter category, click the
(Expand) icon to display all the filter selections with the filter category and the filter tags. To remove a selected filter category, click the ![]() (Delete) icon or click the X in the filter tag to remove a specific selection within the filter category and the list will refresh.
(Delete) icon or click the X in the filter tag to remove a specific selection within the filter category and the list will refresh.
The Source menu allows you to filter the security events that were created from Cisco Secure Cloud Analytics (native sources) and integrated products. All sources are automatically shown by default.
Click the Source drop-down list and check the check boxes next to the product sources to filter the security events displayed. When you select a single source in the filter, the name of the source is displayed in the Applied Filters area. Click the ![]() (Expand) icon to display all the filter selections with the filter category and the filter tags. To remove a selected filter category, click the
(Expand) icon to display all the filter selections with the filter category and the filter tags. To remove a selected filter category, click the ![]() (Delete) icon or click the X in the filter tag to remove a specific selection within the filter category and the list will refresh.
(Delete) icon or click the X in the filter tag to remove a specific selection within the filter category and the list will refresh.
The number of selections is always visible next to Source in the drop-down menu. Click the ![]() (Clear) icon to remove your selections.
(Clear) icon to remove your selections.
The Severity menu allows you display findings based on the severity level (Critical, High, Medium, Low, Informational, Unknown).
Click the Severity drop-down list and choose the severity level of the security events you want displayed in the list.
Check the Detection findings with related incidents check box to only display security events that have related incidents in the list.
You can reorder the columns in the table and select the columns displayed to customize the table for the data you want to view.
To reorder the table columns, click and drag a column header to the desired position in the table.
Click the ![]() (Settings) icon to open the Table settings drawer and check the check boxes next to the columns you want displayed in the Detection findings table. If custom columns are displayed, click Reset to defaults to reset the table column settings to its default values.
(Settings) icon to open the Table settings drawer and check the check boxes next to the columns you want displayed in the Detection findings table. If custom columns are displayed, click Reset to defaults to reset the table column settings to its default values.
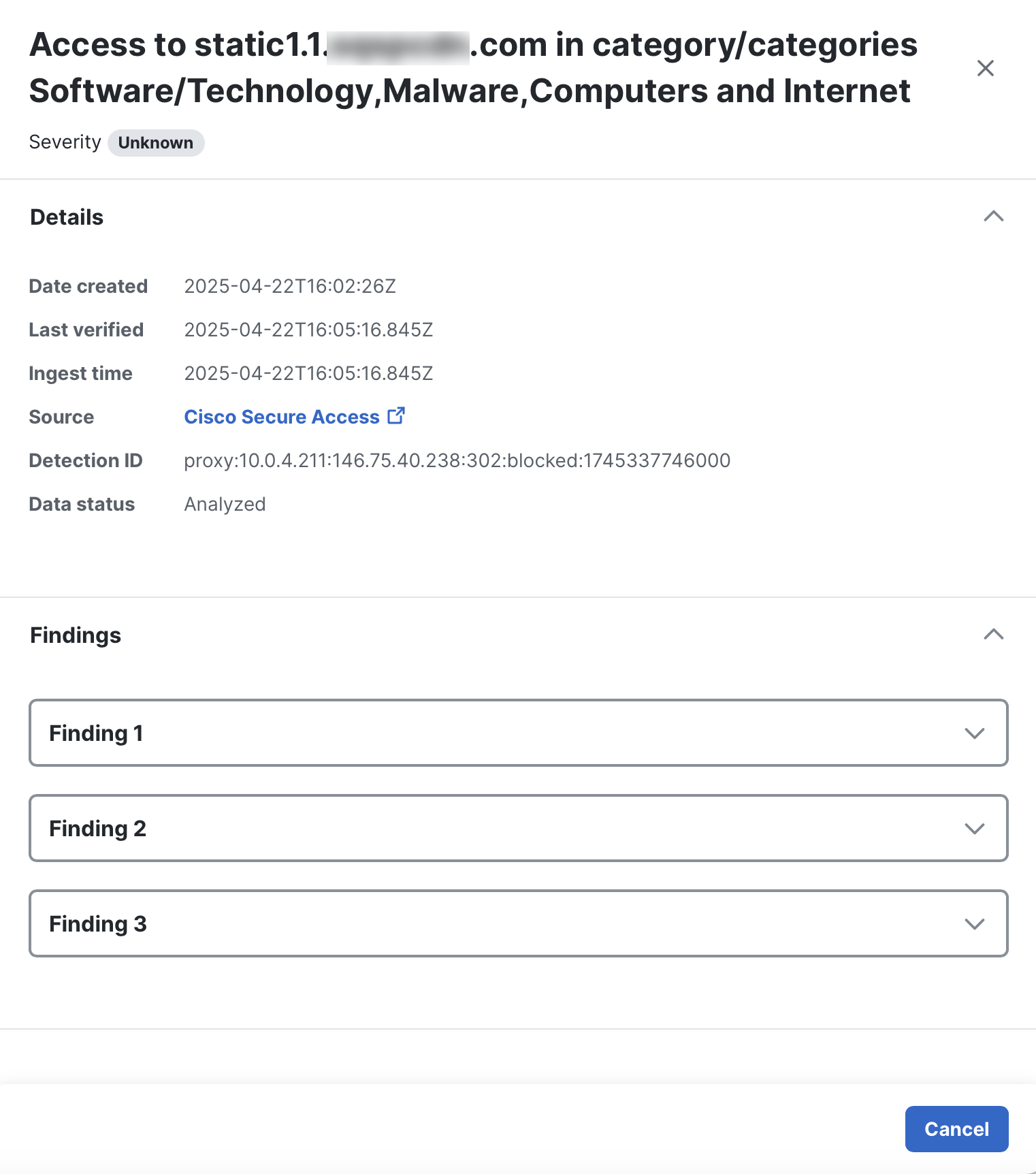
When you click a security event in the list, the Detection Findings drawer opens where you can quickly view the Detection Findings and related Activities derived from the security event. The security event details are displayed using the Industry Standard Open Cybersecurity Schema Framework (OCSF), version 1.4. For details, see Open Cybersecurity Schema Framework.
| Date created | Date and time the security event was created by the source. |
| Last verified | Date and time the security event was last processed by Cisco XDR. |
| Ingest time | Date and time the security event was first received by Cisco XDR. |
| Source | Name of the source product that generated the security event. Click the source link to open the security event in the integrated product. |
| Detection ID | A unique identifier provided by the source for the security event. |
| Data status | Status of whether the event has been analyzed by Cisco XDR for incident correlation. |
|
Related incidents |
Displays all the current incidents that contain the security event. The em dash (—) is displayed if the security event did not contribute to any of the incidents. Click the incident link to open the incident detail in a new tab. For more information on incidents, see Incidents. |
| Findings | Expand the Findings panel to display the Detection Findings for the security event. One security event may result in multiple Detection Findings. Expand a finding to display the Detection Finding and related Activities in JSON format. Click Download or Copy to download or copy the Detection Finding and related Activities displayed in JSON format. |