Secure Email Threat Defense Integration
Secure Email Threat Defense is a cloud-native solution leveraging superior threat intelligence from Cisco Talos. It has an API-enabled architecture for faster response times, complete email visibility, including internal emails, a conversation view for better contextual information, and tools for auto or manual remediation of threats lurking in Microsoft 365 mailboxes.
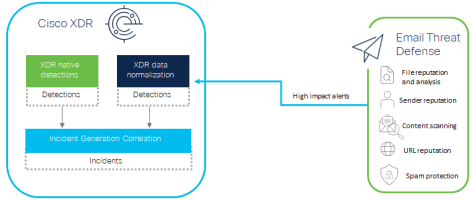
Secure Email Threat Defense integrates with Cisco XDR and Cisco XDR ribbon. XDR allows you to view and act on Secure Email Threat Defense information alongside data from your other Cisco security products. XDR ribbon allows you to navigate between Cisco security products, access casebook, search observables, and view incidents.
The telemetry sources for Secure Email Threat Defense integrated with Cisco XDR are shown below:
-
In the Cisco XDR navigation menu, choose Administration > Integrations.
-
On the Integrations page, click the Cisco tab and navigate to the Secure Email Threat Defense integration.
-
Click Enable. The Secure Email Threat Defense UI is displayed in a new tab.
-
In the Secure Email Threat Defense, authorize Cisco XDR to integrate your Secure Email Threat Defense organization with your Cisco XDR account. For details on how to authorize Cisco XDR in Secure Email Threat Defense, see Authorize Cisco XDR for Secure Email Threat Defense in the Secure Email Threat Defense User Guide.
The Secure Email Threat Defense integration is listed in the My Integrations area on the Cisco XDR Integrations page.
Incidents are groups of correlated events generated using data ingested from your integrated products. By correlating events which could be part of a larger threat into an incident, it reduces the time typically required to investigate individual security alerts or detections. For more information about Cisco XDR Incidents feature, see Incidents.
Malicious messages from Secure Email Threat Defense are correlated to EDR and network alerts by the recipient of the email message in Secure Cloud Analytics. When you enable the Secure Email Threat Defense integration, Cisco XDR analyzes messages and correlates events based on the extracted username of the recipient, allowing suspicious or malicious user activity to be correlated across domains. This excludes common system users, such as administration, system, and root. You can set Secure Cloud Analytics to auto promote the Email Threat Defense alerts to Cisco XDR as incidents; however, by default, this is disabled to reduce noise.
To view incidents with Secure Email Threat Defense data:
-
In the Cisco XDR navigation menu, choose Incidents.
-
Look for Secure Cloud Analytics in the Source column to find incidents generated with Secure Email Threat Defense data.
-
Select an incident and open the Incident Detail page.
-
Click on the Detection page to see events from Secure Email Threat Defense and other sources.
If you do not have any incidents with Secure Email Threat Defense data, you can verify that Cisco XDR is receiving data from Secure Email Threat Defense using the Detection Ingest Status card on the Dashboards page. For more information about Cisco XDR Dashboards, see Dashboards.
To create a new dashboard that includes Detection Ingest Status card:
-
In the Cisco XDR navigation menu, choose Control Center > Dashboards and click Customize in the upper right corner of the Dashboards page.
-
In the My Dashboards area, click Create new dashboard and enter a unique dashboard name in the Dashboard Name field.
-
In the list of integrations, find the Secure Cloud Analytics integration and click the
 (Expand) icon.
(Expand) icon. -
Check the Detection Ingest Status check box to add the card to the dashboard.
-
Click Save.
The new customized dashboard is displayed on the Dashboards page. If no data is displayed in the Detection Ingest Status card for Secure Email Threat Defense, check your integration configuration.
You can perform the following tasks after you integrate Secure Email Threat Defense with Cisco XDR:
-
Investigate - Start a new investigation by searching on suspicious indicators of compromise to extract observables for enrichment. To verify that this integration is working, and to see what kind of data is returned, investigate one or more observables about which you know Secure Email Threat Defense has recent information. For details, see Investigate.
-
Detection findings - View the security events generated by Secure Email Threat Defense to validate the data that is ingested by Cisco XDR for incident generation. For details, see Detection Findings.
-
Dashboard - Add Secure Email Threat Defense cards to a dashboard in Control Center to view data, such as total email traffic by direction. For details, see Configure Dashboards and Cards. For a list of available Secure Email Threat Defense tiles, see Integration Cards.
-
Pivot Menu - Use the Pivot menu to quarantine messages, initiate a search, and move to inbox in Secure Email Threat Defense with the following observables: email address, email message ID, email subject, file name, sender IP, SHA- 256, and URL.