Detection
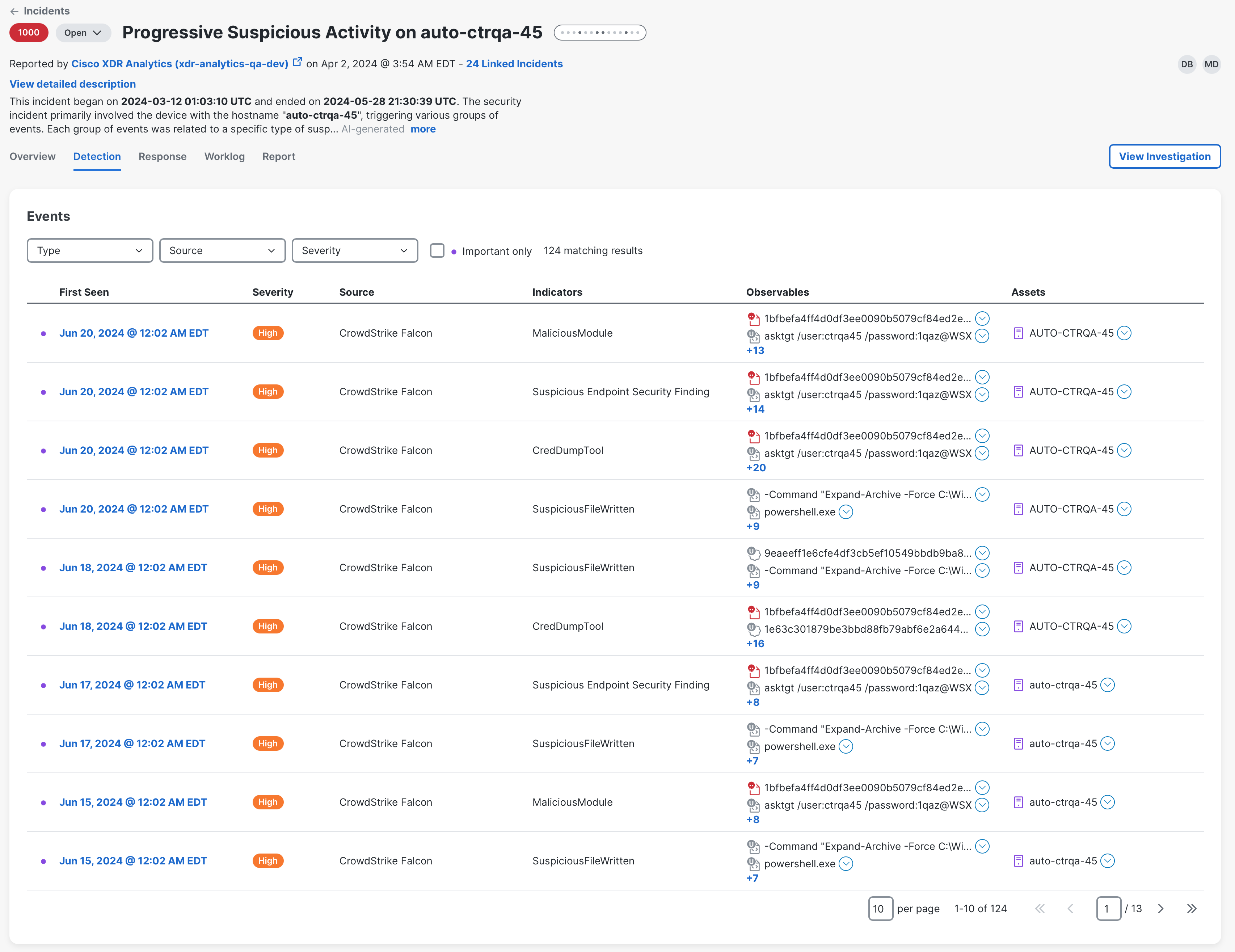
The Detection tab in the incident detail displays data associated with the incident that is derived from security events, judgments, and indicators. By default, the table displays all events from when the incident was created (original events), auto-enriched, or manually investigated.
Security events generated by integrated products are analyzed by the correlation engine in Cisco XDR to determine the relationships between detections, such as shared observables, overlapping timelines, and related attack patterns. When events are determined to be part of the same threat, they are grouped and enriched with additional threat intelligence to create incidents in Cisco XDR. The resulting data is displayed in the Detection tab. For more information on security events, see Detection Findings.
You can filter the types of events to narrow the list of results in the table.
Each row in the table includes data from an event that was initially involved with the incident, or events and indicators included in the saved investigations that are linked to the incident.
|
Column Name |
Description |
|---|---|
|
First Seen |
Date and time of the first finding in a security event created by the source. The events are sorted by timestamp and you can choose to sort newest to oldest (ascending) or oldest to newest (descending) using the |
|
Severity |
The threat level given to the event (Critical, High, Medium, Low, None, Unknown, Info). You can sort the events by highest to lowest severity (Descending) or lowest to highest severity (Ascending) using the sort icon in the column heading. |
|
Source |
Cisco XDR integration or source that produced the event. Click the Source link to open the event in the originating product. You can sort the sources alphabetically using the sort icon in the column heading. |
|
Indicators |
List of indicators the event is related to via a event-of relationship. |
|
Observables |
The first three observables that were contained in the event, and dispositions of the observables taken from verdicts. The observables are color-coded and sorted based on the disposition. If more than three observables were seen in the event, the number of additional observables is displayed in the + more link beneath the list. Click the + more link to open the Observables drawer and view all the observables seen in the event. Use the Search bar in the upper portion of the drawer to quickly search the list of observables and use the Disposition drop-down list and check the check boxes next to the disposition values to narrow the display based on disposition. If you do not choose a disposition, all observables with all dispositions are displayed in the list. Click the Click the |
|
Assets |
The assets that were targeted in the event; where the displayed asset values are based on strong identifier types. The assets are color-coded based the asset type. Click the |
|
Last Seen |
Date and time of the latest finding in a security event created by the source. The events are sorted by timestamp and you can choose to sort newest to oldest (ascending) or oldest to newest (descending) using the This is an optional column that is only available in the Table settings drawer. For details, see Customize Columns. |
|
Name |
Name of the security event defined by the source. This is an optional column that is only available in the Table settings drawer. For details, see Customize Columns. |
You can filter the events by type, source, and severity to narrow the list of results in the table. By default, all the events are displayed.
Filter by Type
The Type menu allows you to display all events, original events, or investigated events.
Click the Type drop-down list and choose which events you want displayed in the list (Original or Investigated). When multiple types are selected, the number of selections is displayed on the label. Click the ![]() (Clear) icon to remove your selections.
(Clear) icon to remove your selections.
Filter by Source
The Source menu allows you filter through events that were promoted from specific integrations.
Click the Source drop-down menu and check the check boxes next to the integrations that promoted the events. When multiple integrations are selected, the number of selections is displayed on the label. Click the ![]() (Clear) icon to remove your selections.
(Clear) icon to remove your selections.
If the event contains 5 or more integrations, a Search bar is visible to enable you to narrow the filter options even further.
Filter by Severity
The Severity menu allows you display events based on the severity level (Critical, High, Medium, Low, None, Unknown, Info).
Click the Severity drop-down menu and choose the severity level of the events and indicators that you want displayed in the list. When multiple severities are selected, the number of selections is displayed on the label. Click the ![]() (Clear) icon to remove your selections.
(Clear) icon to remove your selections.
You can reorder the columns in the table and select the columns displayed to customize the table for the data you want to view.
To reorder the table columns, click and drag a column header to the desired position in the table.
Click the ![]() (Settings) to open the Display Settings drawer and check the check boxes next to the columns you want displayed in the events table. If custom columns are displayed, click Reset to defaults to reset the table column settings to its default values.
(Settings) to open the Display Settings drawer and check the check boxes next to the columns you want displayed in the events table. If custom columns are displayed, click Reset to defaults to reset the table column settings to its default values.
Click Download JSON in the upper right corner of the Detection tab to download all the events in the detections table in JSON format.
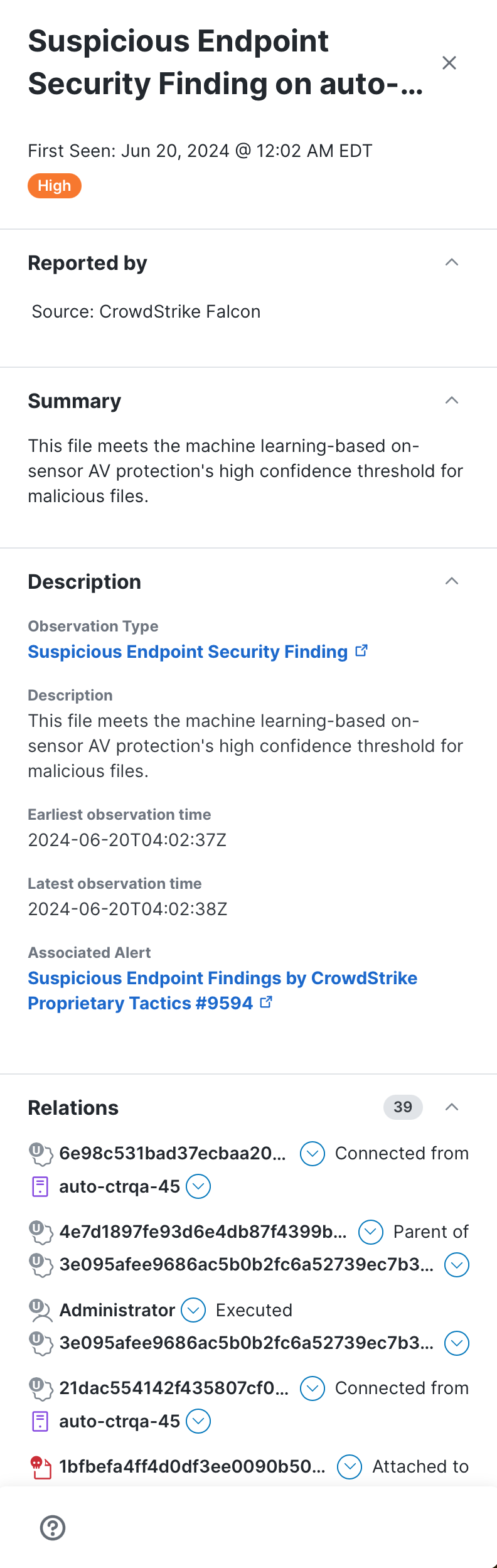
When you click an event in the list, the Event drawer opens where you can quickly view the details of the event.
The Event drawer shows the following information about the selected event.
|
Name |
Name of the security event defined by the source. |
|
Severity |
The severity level assigned to the event. |
|
Reported by |
The source and integration that reported the event. |
|
First seen |
Date and time of the first finding in a security event created by the source. |
|
Last seen |
Date and time of the latest finding in a security event created by the source. |
|
Summary |
Expand the panel to view the condensed description of the event. |
|
Description |
Expand the panel to view the observable type, description, the earliest and latest observation time, and any associated alerts. |
|
Relations |
Expand the panel to view the total number of observables that had a relationship to the selected event, and a list that shows whether the observable was connected to, accessed by, or communicated with the observable. Click the |
|
Indicators |
Expand the panel to view the total number of indicators that the event is related to and a list that shows the incidents. |
|
Assets |
Expand the panel to view the total number of assets that were targeted in the event; where the displayed asset values are based on strong identifier types. The assets are color-coded based on the asset type. Click the |
|
Observables |
Expand the panel to view the total number of observables that were contained in the event, and a list that shows the observables and dispositions taken from verdicts. The observables are color-coded and sorted based on the disposition. Click the |
|
JSON |
Click Copy or Download to copy or download the event data displayed in JSON format for incidents that were created by Cisco Secure Cloud Analytics (Cisco XDR Analytics), depending on the data source. |