Incident Detail
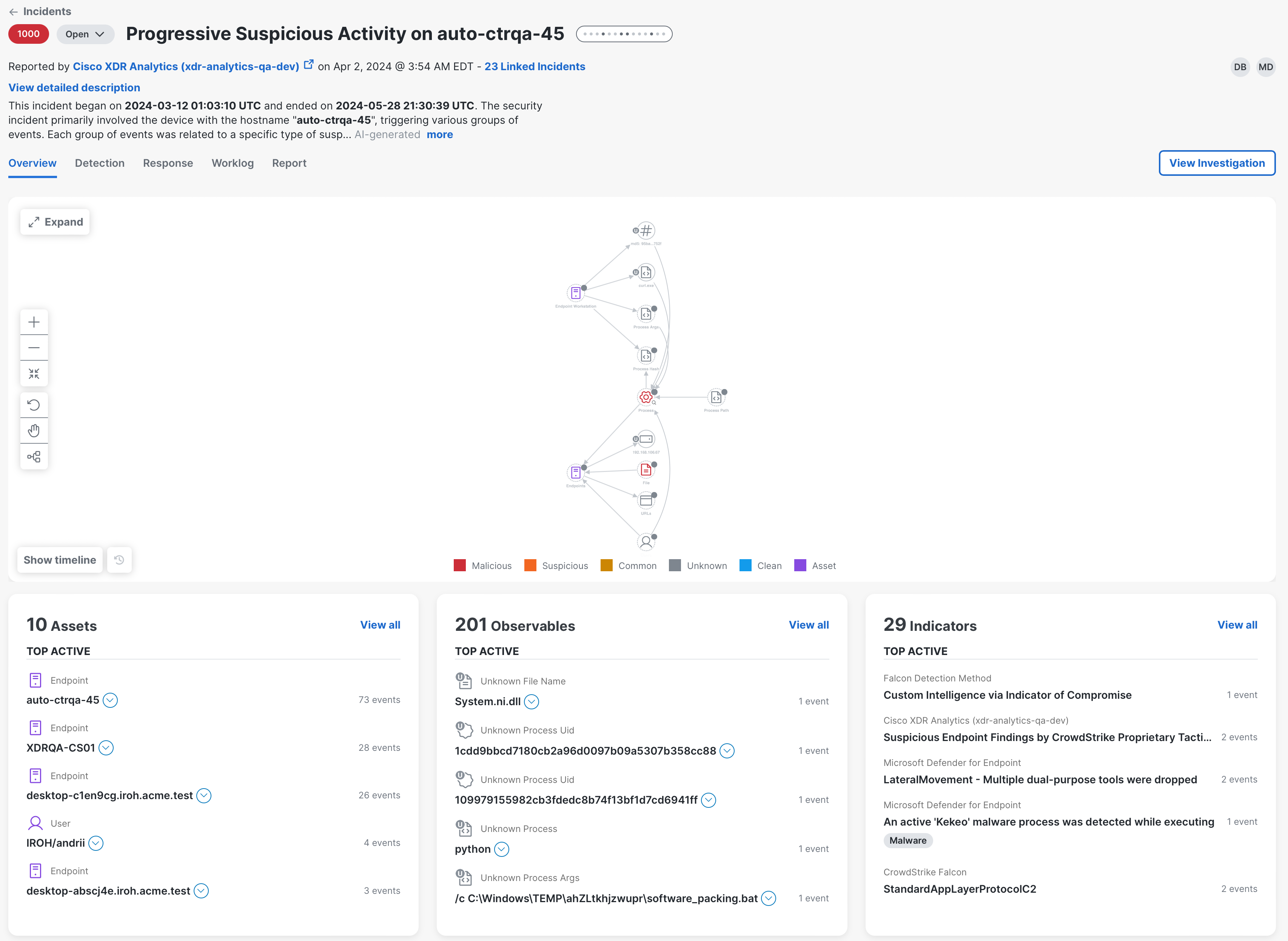
The Incident Detail page provide more information about the incident to help you diagnose, contain, and remediate the threat. The page consists of the header, attack graph, and the following tabs: Overview, Detection, Response Action, and Worklog.
In the header of the Incident Detail page, you can view the status and severity, the incident name and which product reported it along with timestamp, a short description and long description, who has been assigned to the incident, and the MITRE ATT&CK® Tactics. You also have the capability to view the automatic enrichment for the incident as an investigation.
If the incident correlation process identifies the same correlated events between multiple incidents, the newer incidents will automatically merge into the older incident and a message is displayed below the incident description for all incidents to inform the user of the incident merge activity. If the status of a newer incident is New, the status is automatically changed to Closed: Merged once it is merged into the older incident. Incidents are updated as new events occur and if there are no additional common indicators found in 7 days, the newer incident will no longer be updated. A new incident is created if more correlated events and common indicators are seen after 7 days.
From the incident header, you can perform the following tasks:
The incident priority (color-coded based on incident priority score) and the current status that has been assigned to the incident are shown in the upper portion of the header for immediate visibility.
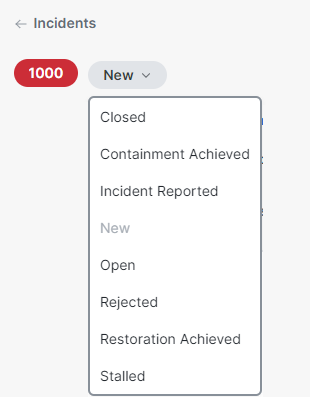
To change the incident status, click the Status drop-down menu and choose a new status. See Available Statuses for more information.
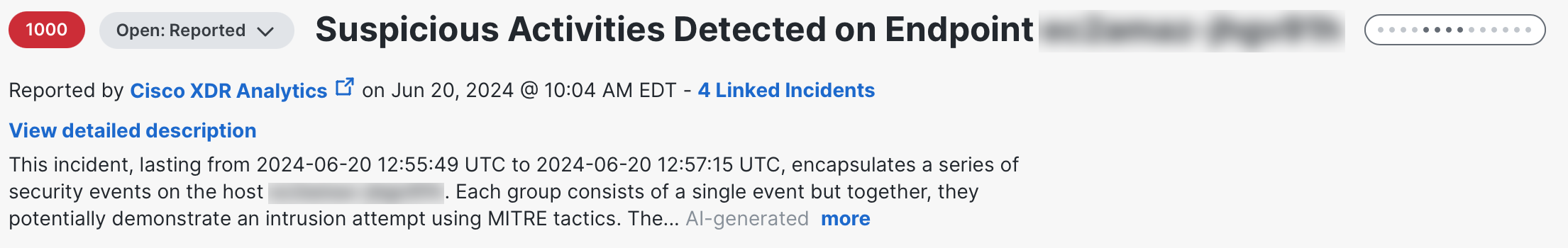
The incident Title and Short description are displayed prominently in the header to provide information about which product reported the incident and a timestamp for when it was reported. The AI-generated label is displayed at the end of the Short description if the description was generated by Cisco AI.
To view the full Short description, click the more link. To collapse the description, click less.
You can edit the incident title and short description by clicking the (Edit) icon. While editing the short description, If you navigate away from the text editor, the short description is automatically saved as a draft for the current browser tab only. The draft content is not available if the same session of Cisco XDR is opened in another browser tab. To restore the short description, return to the content and continue with your edits or click Undo or Use draft to remove or restore the draft content.
Note: The (Edit) icon is not available for AI generated incident title, short description, or long description.
You can also click the reporting product name to pivot to that product and view the compromised event(s) that generated the incident.
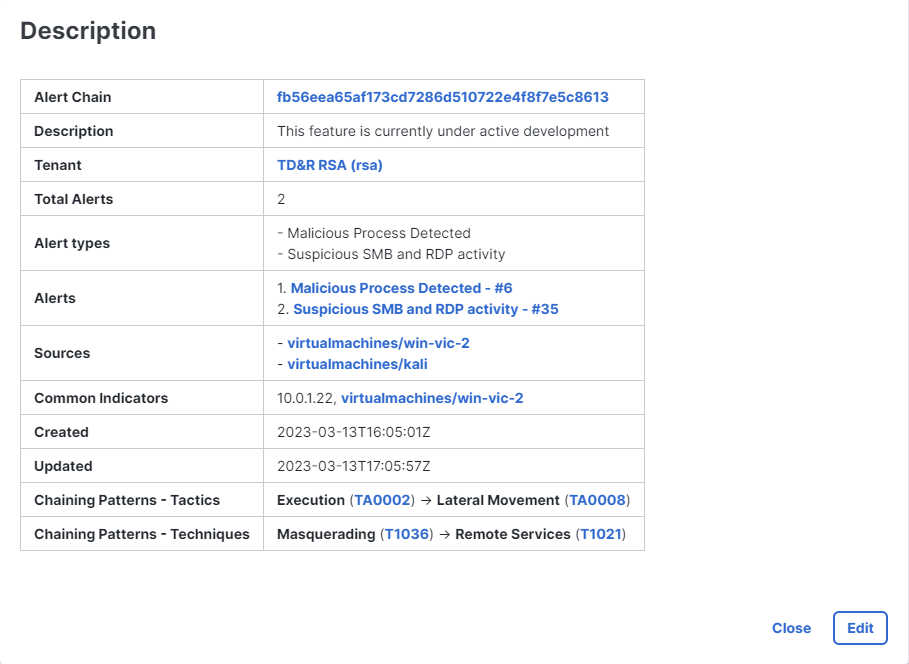
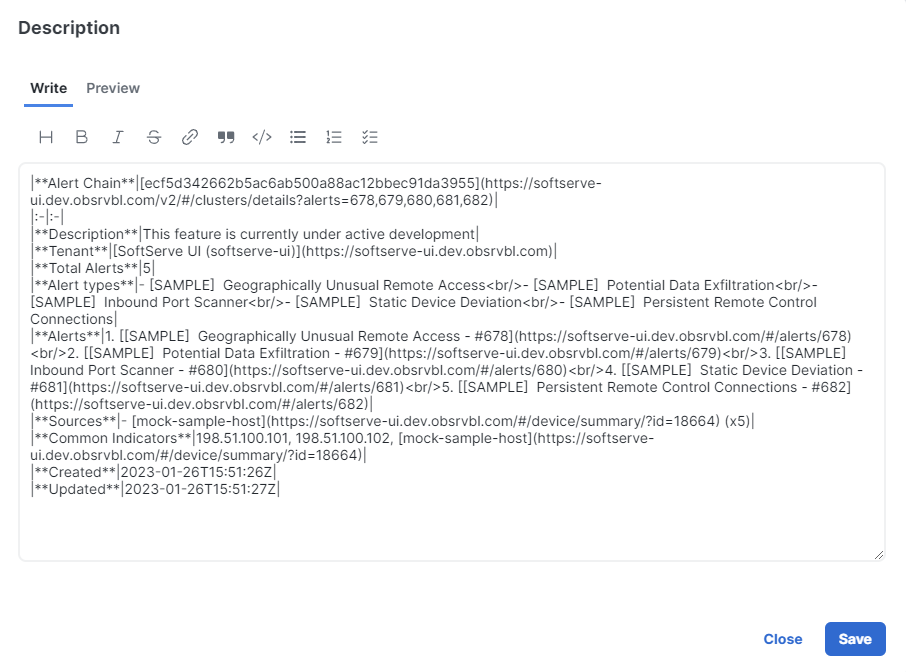
The View detailed description link is displayed just above the Short description in the header. The Detailed description provides a high-level description of the incident, including the source of the incident and the reason for promotion. The summary information varies depending on the reporting product. You can view and edit the Detailed description if the description was not generated by Cisco AI.
-
Click View detailed description in the header to open the Description dialog box.
-
Click Edit to open the editor.
-
On the Write page, enter your changes in markdown format. You can also use the options available in the formatting toolbar.
Note: If you navigate away from the text editor while editing, the description is automatically saved as a draft for the current browser tab only. The draft content is not available if the same session of Cisco XDR is opened in another browser tab. To restore the description, return to the text editor and continue with your edits or click Undo or Use draft to remove or restore the draft content.
-
Optionally, click the Preview tab to view the modified description.
-
Click Save to close the editor.
-
Click Close to exit the Description dialog box.
Note: The AI-generated label is displayed at the bottom of the Description dialog box if the description was generated by Cisco AI.
Note: The Edit button is not available in the Description dialog box if the detailed description was generated by Cisco AI.
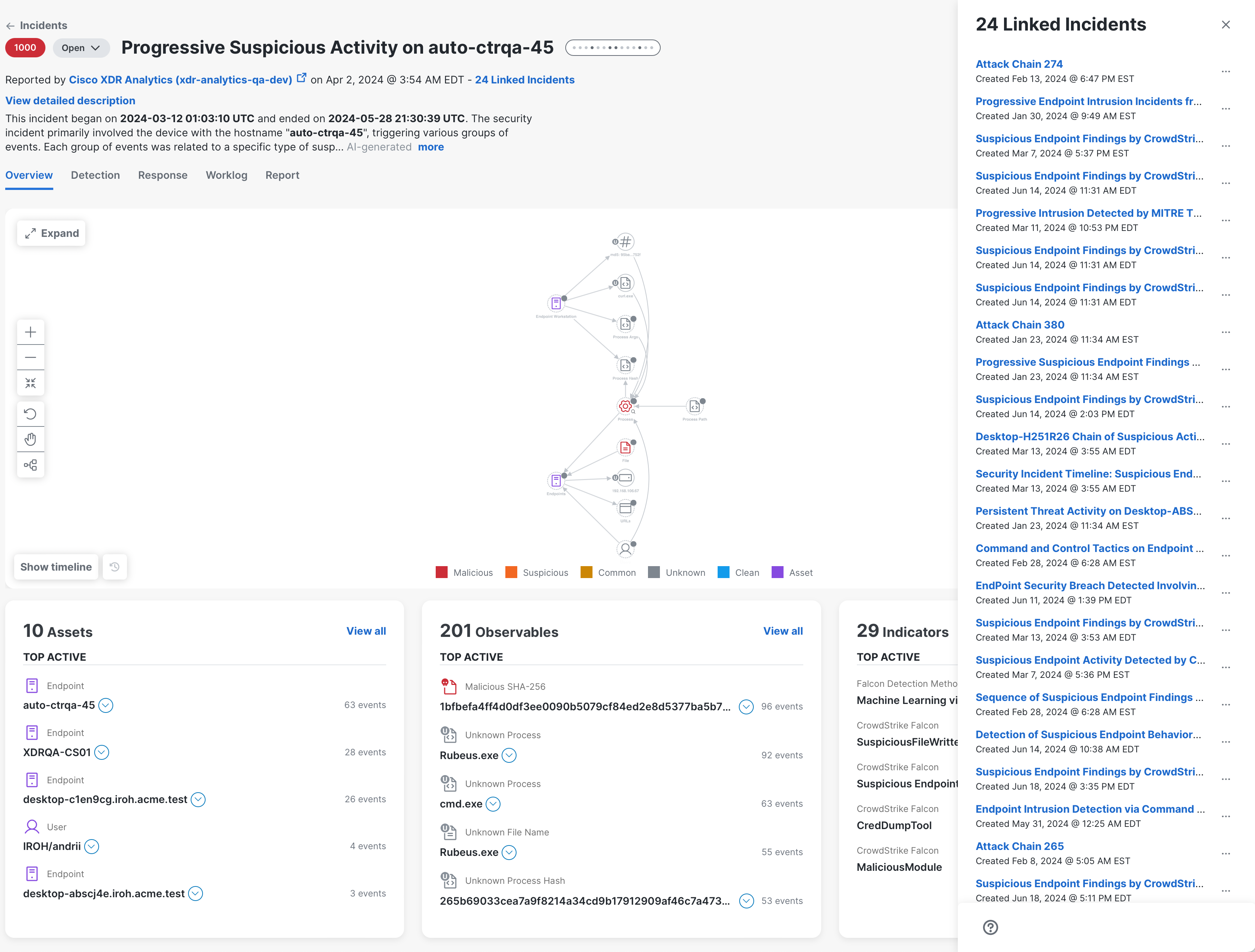
The number of linked incidents is displayed beneath the incident title. Click Linked Incidents to open the Linked Incidents drawer and view the other incidents that are linked to the selected incident.
The Linked Incidents drawer displays the total number and list of incidents that are linked to the selected incident along with the date it was linked. Click the linked incident name to open the incident and view it in a new tab.
To unlink an incident, click the ![]() (Ellipsis) icon next to the incident you want to unlink and choose Unlink from the drop-down menu. A message is displayed indicating the Incident was successfully unlinked and removes it from the drawer.
(Ellipsis) icon next to the incident you want to unlink and choose Unlink from the drop-down menu. A message is displayed indicating the Incident was successfully unlinked and removes it from the drawer.
To close the drawer, click the (Close) icon in the upper right corner.
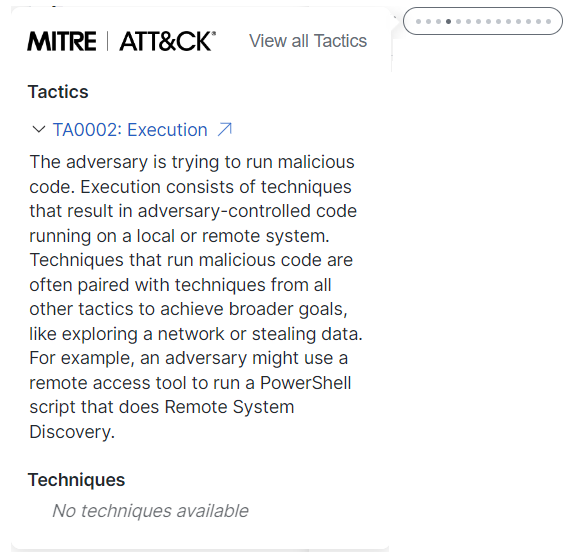
The MITRE tactic tag shows the MITRE ATT&CK® tactics impacting the incident based on the Financial Risk Score, which indicates the probability of financial impact if the MITRE ATT&CK® patterns are not mitigated—the higher the score, the higher the probability of impact. If there are two or more tactics impacting the incident, the number of tactics is also displayed in the MITRE tactic tag.
Click the MITRE tactic tag to view the MITRE Tactic popup showing a list of specific MITRE ATT&CK tactics and techniques impacting the incident. The MITRE ATT&CK Coverage Map link opens the MITRE ATT&CK Coverage Map page. For details, see MITRE ATT&CK Coverage Map.
Click the ![]() (Expand) icon to view all the techniques for each tactic listed. Click the
(Expand) icon to view all the techniques for each tactic listed. Click the ![]() (New Tab) icon next to the tactic name to view the tactic details on the MITRE ATT&CK Enterprise Tactics page in a new tab and the technique link displays the technique details on the MITRE ATT&CK Enterprise Techniques page in a new tab.
(New Tab) icon next to the tactic name to view the tactic details on the MITRE ATT&CK Enterprise Tactics page in a new tab and the technique link displays the technique details on the MITRE ATT&CK Enterprise Techniques page in a new tab.
Click View events to view all events related to the incident on the Detections tab in the incident detail. For details, see Detection.
Click the View Investigation button to open the Investigate page and view a more in-depth graphical and tabular view of the events that were found from the automatic enrichment that was performed when the incident was created.
Note: The View Investigation button will only be displayed for higher priority incidents that have malicious or suspicious observables in the events.
When the incident detail for a new, unassigned incident is first viewed by a user with an Incident Responder or Security Analyst role, the user who viewed the incident is automatically assigned to it and the incident status is changed to Open. You can assign or unassign users from the Assigned field in the header.
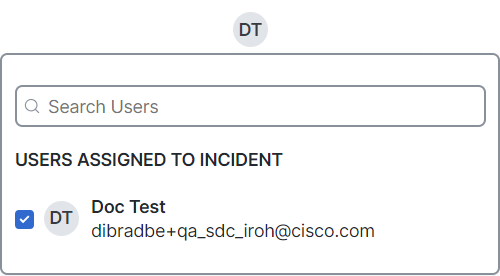
When the incident is assigned, an avatar with the user's initials is displayed and you can hover over the avatar to view the user's full name in a tooltip.
-
Click any of the avatars in the Assigned field in the header.
-
Begin entering the user's name in the Search Users field and then check the check box next to their name in the list that is displayed.
-
Click outside the Assignee menu to apply your selection.
-
When an incident is assigned to another user, they will receive a notification in the
 (Notifications) icon in the Cisco XDR header and ribbon. For more information about this feature, see the Notifications help topic.
(Notifications) icon in the Cisco XDR header and ribbon. For more information about this feature, see the Notifications help topic.
The list of users already assigned to incident are displayed in the list with the check box checked.
To remove an assignee, uncheck the check box next to their name.
When an incident is selected, a URL is generated in the browser address bar that you can copy and share the incident with others. In addition, if you click a tab on the Incident Detail page, the tab name is appended to the URL.
The Overview tab in the incident detail provides an attack graph in the upper portion of the page and overall metric counts of the most important data within the selected incident in the metric cards in the lower portion of the page.
The attack graph displays a compacted relationship view of the investigation of events that caused the incident to be promoted. This view provides a linear progression of the attack at a high level. The Timeline panel beneath the attack graph displays a color-coded timeline (based on disposition) of the volume of events at different points in time.
The metric cards in the lower portion of the page provide a summary of the top active assets, observables, and indicators to help you quickly understand the incident from one view. The metrics are based on the total number of events for the selected incident. Open the drawer on each card to view all assets, observables, and indicators associated with the incident, and to view in the investigation.
For more information, see the Incident Overview help topic.
The Detection tab in the incident detail displays data associated with the incident that is derived from events, judgments, and indicators. You can filter the types of events to narrow the list of results in the table.
Each row in the table includes data from an event that was initially involved with the incident, or events and indicators included in the saved investigations that are linked to the incident. The table displays the date and time the event was first observed, severity, source, indicators that the event is related to via a event-to relationship, and observables and assets seen in the event.
For more information, see the Detection help topic.
The Response tab in the incident detail displays a playbook template to assist in building effective incident response plans, processes, and procedures. Use the response tasks on this page to identify, contain, and eradicate the threat, and then restore systems to recover from the threat. Workflows are available for execution to automate some of the response tasks; notes are available to document your findings throughout the incident response process.
For more information, see the Response Tasks help topic.
The Evidence tab in incident detail allows you to acquire and view forensic data from assets within an incident and connect to the assets using a remote shell for remediation purposes. Use the acquired data for further analysis and investigation in the XDR Forensics UI.
For more information, see the Evidence help topic.
The Worklog tab in the incident detail is used to enter notes about the findings while investigating the incident and to view the audit log of changes that have been made to the incident.
By default, all events are displayed. Click the ![]() (Filters) icon to filter the list of events.
(Filters) icon to filter the list of events.
To sort the list of data, click the Sort by filter menu and choose Sort by Newest or Sort by Oldest.
For more information, see the Worklog help topic.
The Report tab in the incident detail displays AI-generated incident summary information that can be downloaded in a report format. This information can be edited and formatted in markdown, and then downloaded in a single file to your local computer. If something changes in the incident, the sections can be regenerated to get fresh AI-generated content and then, if necessary, edited and downloaded again to get an updated report file.
For more information, see the Report help topic.