Microsoft Defender for Office 365 GCC Integration
Note: This integration is with Microsoft's GCC environment, and it will forward those logs to Cisco XDR's environment located in AWS Commercial Cloud. Be aware of this before choosing to configure this integration.
Microsoft Defender for Office 365 GCC is a cloud-based email filtering service that helps protect your organization against advanced threats delivered via email and collaboration tools, like phishing, business email compromise, and malware attacks.
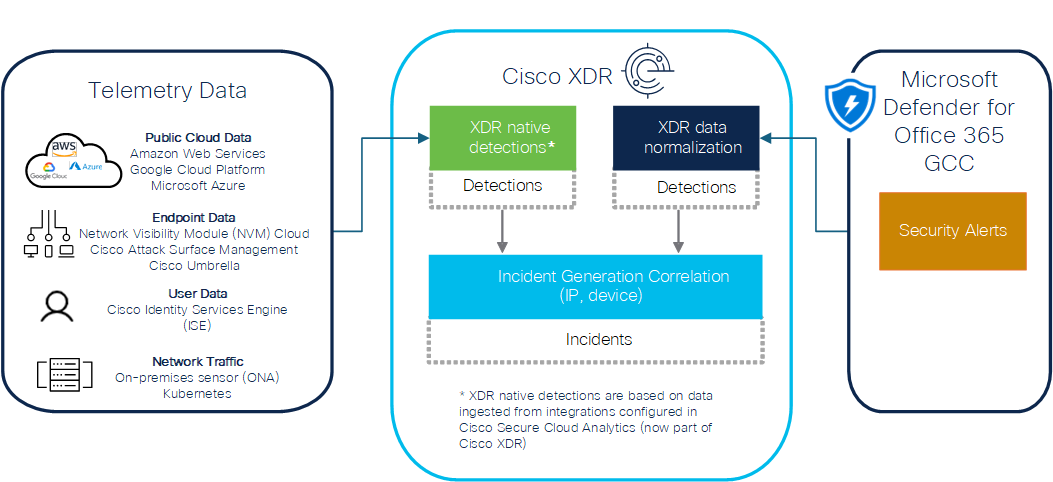
Integration with Microsoft Defender for Office 365 GCC allows you to incorporate Microsoft Defender for Office 365 GCC detections alongside detections from other telemetry sources into Cisco XDR's overall incident detection and correlation capabilities.
-
In the Cisco XDR navigation menu, choose Administration > Integrations.
-
On the Integrations page, click the Third-Party tab and navigate to the Microsoft Government Community Cloud (GCC) integration.
-
Click the plus sign (+) in the lower-right corner of the card. The Microsoft Government Community Cloud (GCC) integration page is displayed.
-
Expand the Integration Guide area and follow the instructions on how to add the Microsoft Defender for Office 365 GCC integration in Cisco XDR.
Incidents are groups of correlated events generated using data ingested from your integrated products. By correlating events which could be part of a larger threat into an incident, it reduces the time typically required to investigate individual security alerts or detections. For more information about Cisco XDR Incidents feature, see Incidents.
When you enable the Microsoft Defender for Office 365 GCC integration, Cisco XDR ingests the security alerts that are sent by Microsoft Defender for Office 365 GCC and uses them for incident correlation.
To view incidents with Microsoft Defender for Office 365 GCC data:
-
In the Cisco XDR navigation menu, choose Incidents.
-
Look for Microsoft Defender for Office 365 GCC in the Source column to find incidents generated with Microsoft Defender for Office 365 GCC data.
-
Select an incident and open the Incident Detail page.
-
Click on the Detection page to see events from Microsoft Defender for Office 365 GCC and other sources.
You can perform the following tasks after you integrate Microsoft Defender for Office 365 GCC with Cisco XDR:
-
Investigations - Start a new investigation into email addresses, URLs, email subjects, message IDs, IPs, domains, or file hashes, and the results will include any records of them found in your Microsoft Defender for Office 365 GCC. To verify that this integration is working, and to see what kind of data is returned, investigate one or more observables about which you know Microsoft Defender for Office 365 GCC has recent information. For details, see Investigate.
-
Automation:
-
Atomic Actions -The Mail atomic actions for Microsoft Graph Security API can be used as building blocks in custom workflows for Microsoft Defender for Office 365 GCC. These can be found as available Actions in the left menu of the Workflow Editor. See Atomic Actions and Workflows.
-
Target - The Microsoft Defender for Office 365 GCC target is automatically created for out-of-box and custom workflows. See Targets Created From Integrations.
-
Playbooks - An Automation system workflow that uses Microsoft Defender for Office 365 GCC and is included in the Cisco Managed Incident Playbook can be used to quarantine, delete, or move email messages. See Containment, Eradication, and Recovery on the Response page.
-