Create Deployment
Note: Only users with an Administrator role can create deployments.
You use the Create Deployment page to add a new Secure Client deployment in Cisco XDR. Once the deployment is created, it is displayed on the Deployments page.
Generally, there are the following options to select from in each Version Control drop-down list:
Note: The options are subject to change at any time and don’t have to be consistent across the different products.
- Latest – The most recent version of the connector. It will automatically be updated each time a new version is released.
- Recommended – The version with the largest user base that has been available for a while without any major issues. It will automatically be updated each time a new recommended version is released.
- Specific release versions
Note: When a specific release version is deprecated, the module will automatically be disabled, and the version will appear as "N/A" on the Deployment Management page. If you have selected a specific release version that has been deprecated, you will need to edit the deployment and manually update the release version.
To create a new deployment:
-
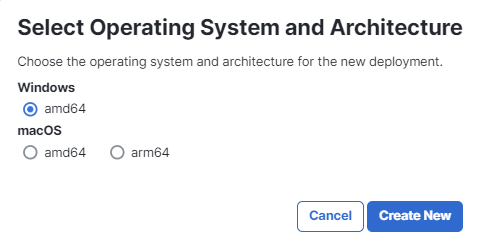
Click Create New on the Deployments page.
-
Select the operating system and architecture for the deployment, then click Create New.
Note: The following steps may vary depending on the selected operating system and architecture. For supported modules on the selected operating system and architecture, see the Operating System and Architecture Support section.
-
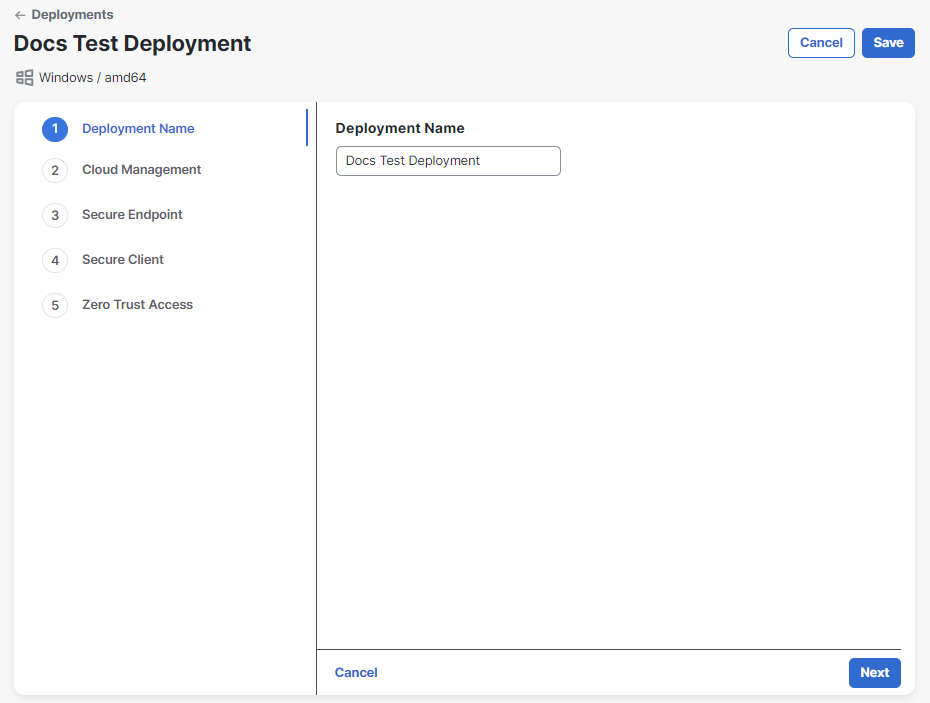
Enter a name for the deployment, then click Next.
-
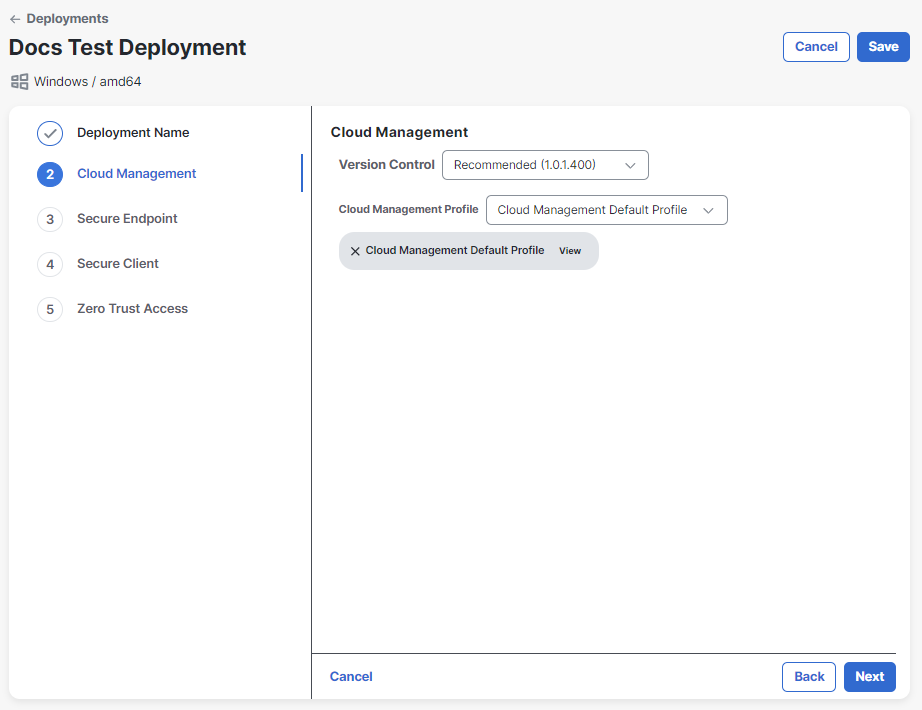
Choose the version and profile for the Cloud Management module from the drop-down lists. If you need to create a new Cloud Management profile, click the
 (Add) icon to create or upload a new profile. Then click the
(Add) icon to create or upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list. After choosing the version and profile, click Next.
(Refresh) icon to update the profile drop-down list. After choosing the version and profile, click Next.Note: If you do not specify a Cloud Management profile when creating a deployment, a profile will be generated and applied at the time of installation, in which default Cloud Management settings are used. This profile cannot be viewed or edited and is subject to change. If this is not desirable, we recommend that you create a unique Cloud Management profile to assign to deployments that don't already have one or use the Cloud Management Default Profile. For details on creating a Cloud Management profile, see the Profile Configuration help topic.
The Cloud Management module will connect to these regional API endpoints:
-
North America (NAM)
-
admin.prod.nam.csc.cisco.com
-
identify.prod.nam.csc.cisco.com
-
pacman.prod.nam.csc.cisco.com
-
cisco-ucb-nam-pass-repo.s3.us-east-1.amazonaws.com
-
cisco-ucb-nam-catalog-repo.s3.us-east-1.amazonaws.com
-
-
Europe (EU)
-
admin.prod.eu.csc.cisco.com
-
identify.prod.eu.csc.cisco.com
-
pacman.prod.eu.csc.cisco.com
-
cisco-ucb-eu-pass-repo.s3.eu-west-1.amazonaws.com
-
cisco-ucb-eu-catalog-repo.s3.eu-west-1.amazonaws.com
-
-
Asia, Pacific, Japan, China (APJC)
-
admin.prod.apjc.csc.cisco.com
-
identify.prod.apjc.csc.cisco.com
-
pacman.prod.apjc.csc.cisco.com
-
cisco-ucb-apjc-pass-repo.s3.ap-northeast-1.amazonaws.com
-
cisco-ucb-apjc-catalog-repo.s3.ap-northeast-1.amazonaws.com
-
Note: There is not an option to configure a proxy for the Cloud Management module.
-
-
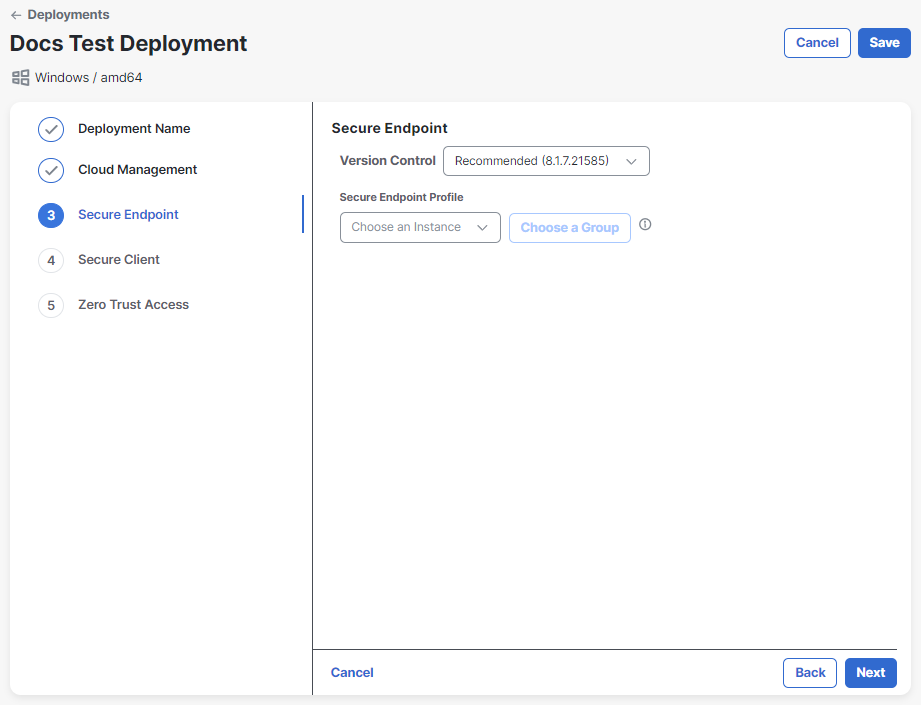
Click the toggle to enable Secure Endpoint. If you do not want to include the Secure Endpoint module, do not click the toggle and proceed to step 9.
-
Choose the version for the Secure Endpoint module you want to deploy.
-
Choose the Secure Endpoint Instance from the drop-down list. If you have integrated more than one Secure Endpoint organization with Cisco XDR, they’ll be listed here.
-
Choose the Secure Endpoint Group that the Secure Client endpoints will join. See Groups in the Secure Endpoint User Guide for more information about creating and configuring a group. If you need to edit the Secure Endpoint instance or group, click Replace Bootstrap Profile.
-
Click Next.
-
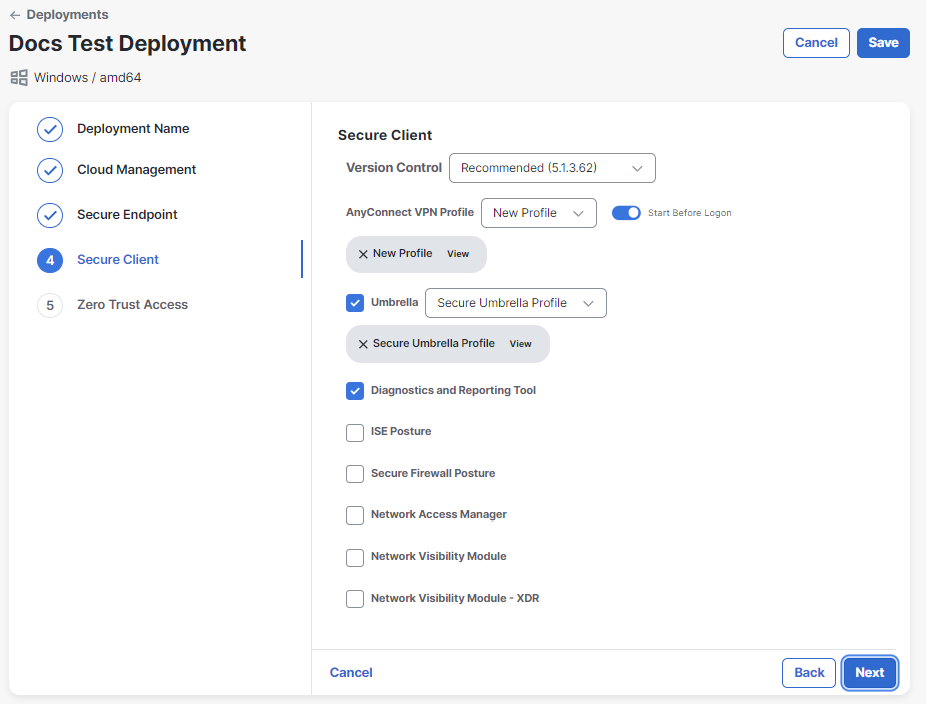
Click the toggle to enable the Secure Client AnyConnect VPN module and related settings. If you do not want to include the AnyConnect VPN module, do not click the toggle and proceed to step 14.
-
Choose a version and profile for the AnyConnect VPN module you want to deploy from the drop-down lists. If you need to create a new AnyConnect VPN profile, click the
 (Add) icon to create or upload a new profile. Then click the
(Add) icon to create or upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list. For details on creating a VPN profile, see the Profile Configuration help topic.
(Refresh) icon to update the profile drop-down list. For details on creating a VPN profile, see the Profile Configuration help topic.Note: By default, a VPN profile will be deployed with the name CloudManaged.xml on the device. To specify the name, append .xml to the profile name (for example, VPN_TEST.xml).
-
To enable the Start Before Logon feature which allows users to establish their VPN connection to the enterprise infrastructure before logging onto Windows, click the toggle.
-
Check the check boxes to enable the following optional settings:
- Umbrella - The Umbrella dashboard is where you obtain the profile (OrgInfo.json) for the Cisco Secure Client Umbrella Roaming Security module to include in your deployment. From the Umbrella dashboard, you also manage policy and activity reporting for the roaming client. If you need to create a new Umbrella profile, click the
 (Add) icon to upload a new profile. Then click the
(Add) icon to upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list.
(Refresh) icon to update the profile drop-down list. - Diagnostics and Reporting Tool - DART is the Diagnostics and Reporting Tool that you can use to collect data for troubleshooting Cisco Secure Client installation and connection problems. DART assembles the logs, status, and diagnostic information for Cisco Technical Assistance Center (TAC) analysis.
- ISE Posture - The ISE Posture module uses the OPSWAT v3 or v4 library to perform posture checks. With an initial posture check, any endpoint that fails to satisfy all mandatory requirements is deemed non-compliant. An administrator can choose to use the standalone editor to create the posture profile and then upload it to ISE. If you need to create a new ISE Posture profile, click the
 (Add) icon to create or upload a new profile. Then click the
(Add) icon to create or upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list.
(Refresh) icon to update the profile drop-down list. - Secure Firewall Posture - Secure Firewall Posture automatically identifies operating systems and service packs on any remote device establishing an AnyConnect VPN client session. You can also configure Secure Firewall Posture to inspect the endpoint for specific processes, files, and registry keys. It performs all of these inspections before full tunnel establishment to distinguish between corporate-owned, personal, and public computers.
- Network Access Manager - The Network Access Manager is client software that provides a secure Layer 2 network in accordance with its policies. It detects and selects the optimal Layer 2 access network and performs device authentication for access to both wired and wireless networks. Network Access Manager manages user and device identity and the network access protocols required for secure access. Although Network Access Manager is part of Cisco Secure Client 5.0, the Network Access Manager Profile Editor within Cisco XDR will not be available for 5.0. If you need to create a new Umbrella profile, click the
 (Add) icon to upload a profile that was created by a standalone editor outside of Cisco XDR or one that was exported from ASDM. Then click the
(Add) icon to upload a profile that was created by a standalone editor outside of Cisco XDR or one that was exported from ASDM. Then click the  (Refresh) icon to update the profile drop-down list.
(Refresh) icon to update the profile drop-down list. - Network Visibility Module - The Network Visibility Module (NVM) collects rich flow context from an endpoint on or off premises and provides visibility into network connected devices and user behaviors. The enterprise administrator can then do capacity and service planning, auditing, compliance, and security analytics. If you need to create a new Network Visibility Module profile, click the
 (Add) icon to create or upload a new profile. Then click the
(Add) icon to create or upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list.
(Refresh) icon to update the profile drop-down list. - Network Visibility Module - XDR - This module collects rich flow context from an endpoint to provide more visibility into your network. Network Visibility Module - XDR creates a flow record of every connection from an endpoint and forwards the data over a secure connection to the cloud. Deployments using Network Visibility Module - XDR can send telemetry to Cisco XDR without needing an on-premises collector. If you need to create a new Network Visibility Module - XDR profile, click the
 (Add) icon to create or upload a new profile. Then click the
(Add) icon to create or upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list.
(Refresh) icon to update the profile drop-down list.
The Network Visibility Module - XDR module will connect to these regional API endpoints:- North America (NAM)
intake.prod.nam.tmc.nvm.csc.cisco.com
- Europe (EU)
intake.prod.eu.tmc.nvm.csc.cisco.com
- Asia, Pacific, Japan, China (APJC)
intake.prod.apjc.tmc.nvm.csc.cisco.com
- North America (NAM)
- Umbrella - The Umbrella dashboard is where you obtain the profile (OrgInfo.json) for the Cisco Secure Client Umbrella Roaming Security module to include in your deployment. From the Umbrella dashboard, you also manage policy and activity reporting for the roaming client. If you need to create a new Umbrella profile, click the
-
Click Next.
-
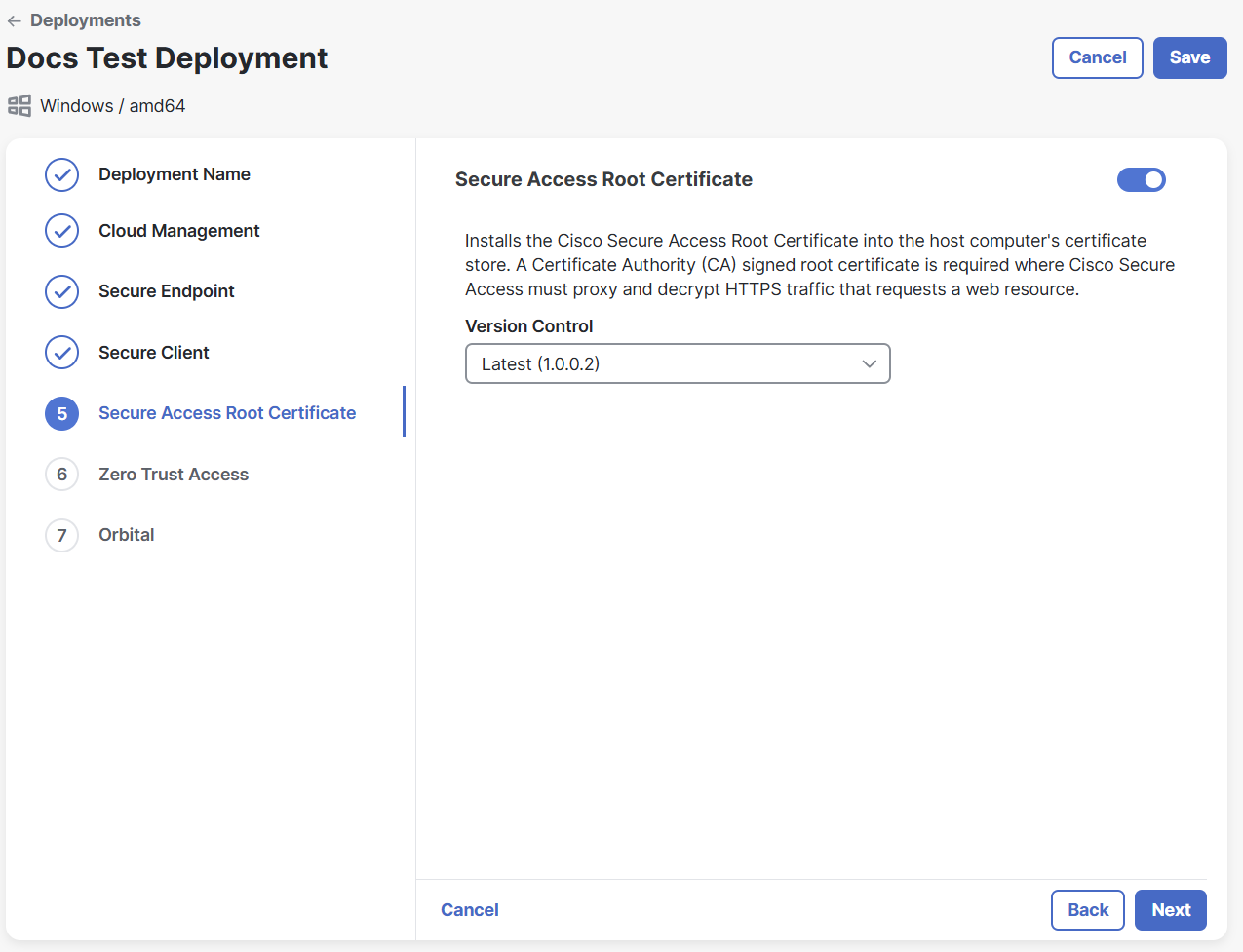
Click the toggle to enable the Secure Access Root Certificate module. If you do not want to include the module, do not click the toggle and proceed to step 17.
-
Choose a version for the Secure Access Root Certificate module from the drop-down list.
-
Click Next.
-
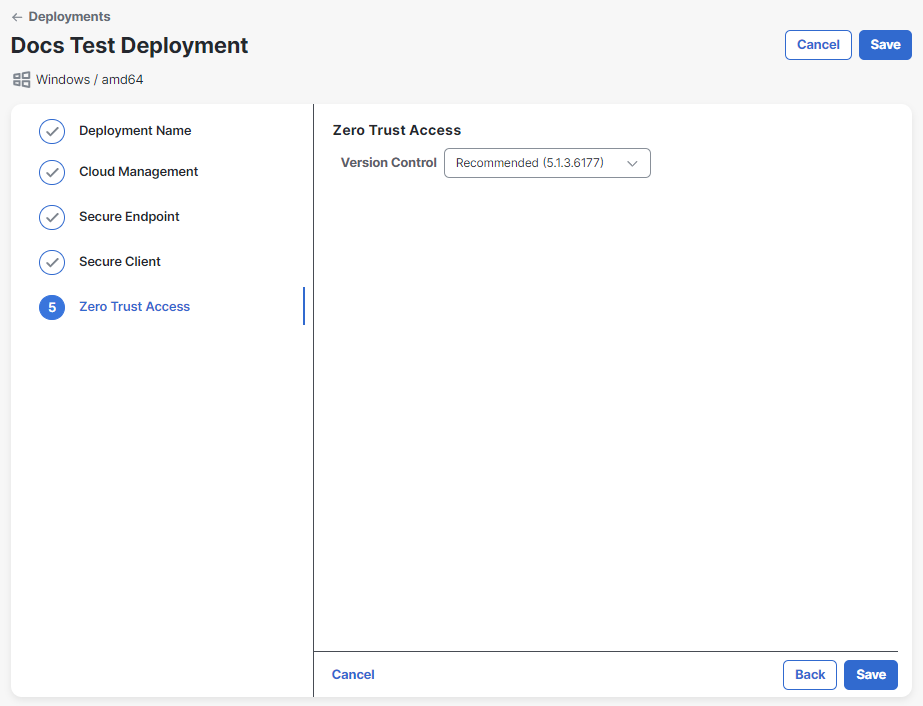
If you selected AnyConnect VPN version 5.1.3.62 or later, you can enable the Zero Trust Access module. Zero Trust Access reduces the attack surface by hiding applications and expands your level of knowing, understanding, and controlling who and what is on your network. For more information, see the Zero Trust Access Module documentation in the Cisco Secure Client (including AnyConnect) Administrator Guide. Click the toggle to enable the Zero Trust Access module. If you do not want to include the Zero Trust Access module, do not click the toggle and proceed to step 20.
-
Choose a version and profile for the Zero Trust Access module you want to deploy from the drop-down lists. If you need to create a new Zero Trust Access profile, click the
 (Add) icon to upload a new profile. Then click the
(Add) icon to upload a new profile. Then click the  (Refresh) icon to update the profile drop-down list. For details on creating a Zero Trust Access profile, see the Profile Configuration help topic.
(Refresh) icon to update the profile drop-down list. For details on creating a Zero Trust Access profile, see the Profile Configuration help topic. -
Click Next.
-
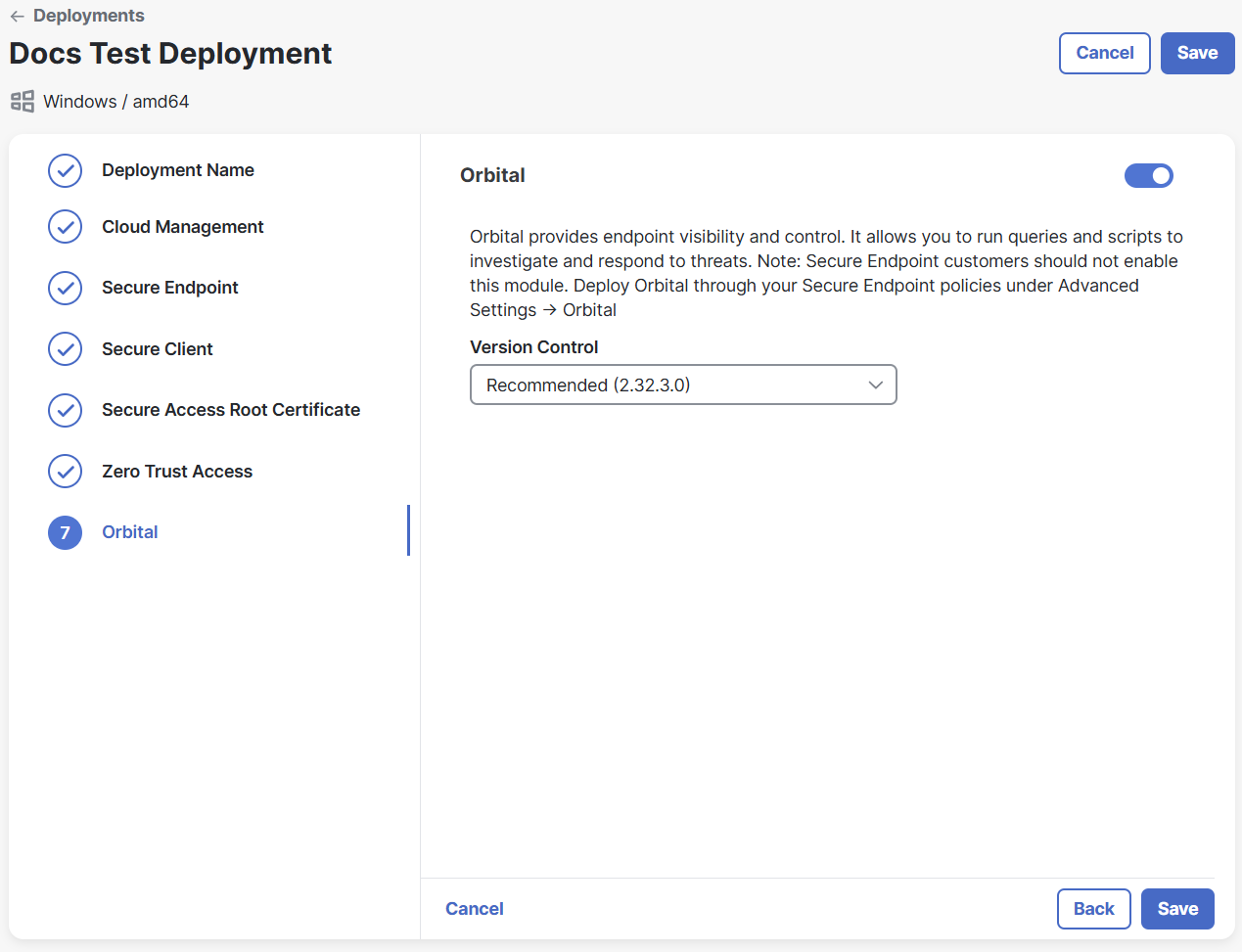
Click the toggle to enable Orbital module. If you do not want to include the module, do not click the toggle and proceed to step 23.
Note: Secure Endpoint customers should not enable this module and should deploy Orbital through Secure Endpoint.
-
Choose a version for the Orbital module from the drop-down list.
-
Click Next.
-
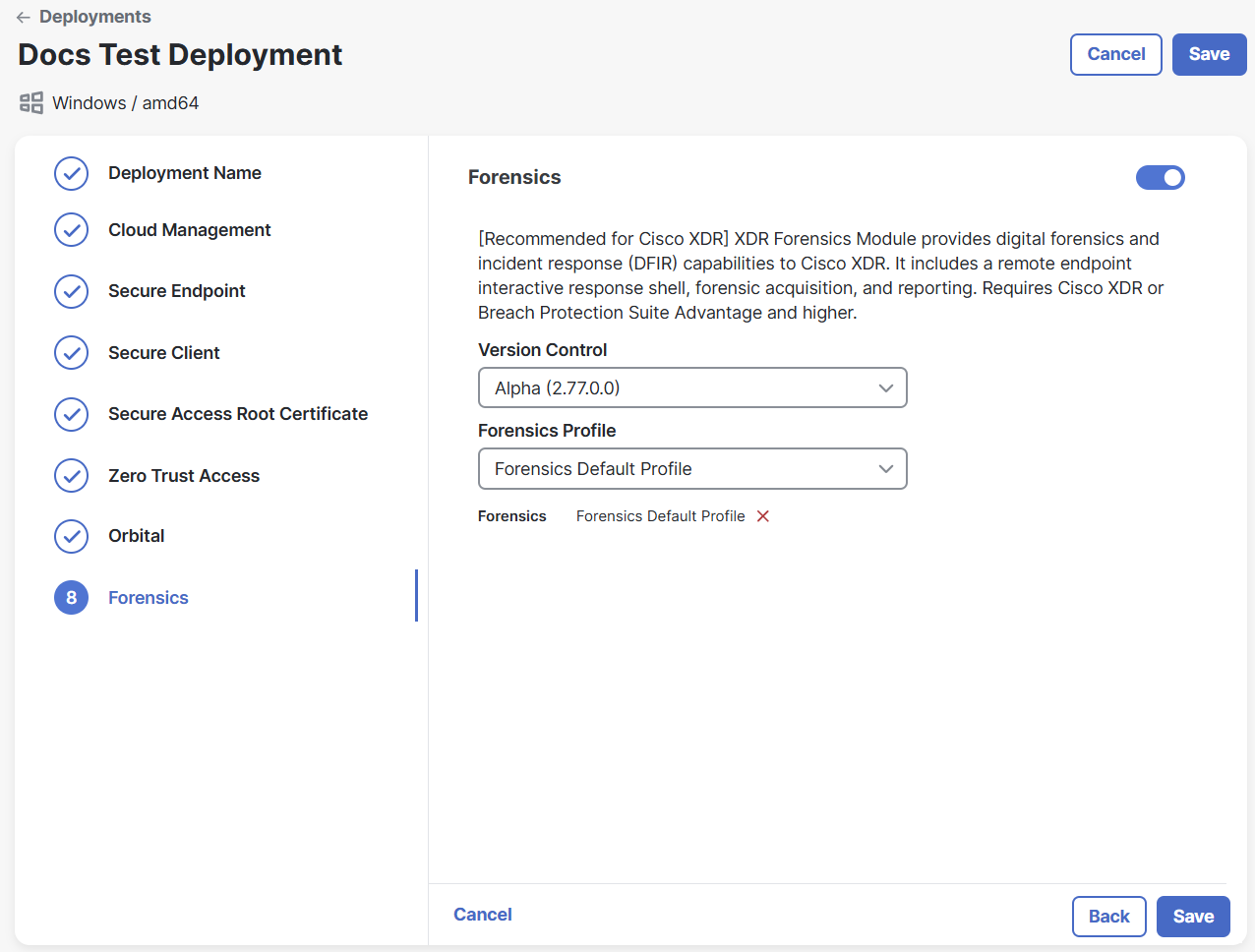
Click the toggle to enable XDR Forensics. XDR Forensics provides remote data collection from endpoints, remote shell, and advanced digital forensics capabilities. If you enable this module for your deployment, you will be able to acquire forensic data from assets within an incident. For more information, see the XDR Forensics help topic. If you do not want to include the XDR Forensics module, do not click the toggle and proceed to step 26.
Note: XDR Forensics is only available for customers with Cisco XDR Advantage or Cisco XDR Premier licensing tier.
-
Choose a version and profile for the XDR Forensics module you want to deploy from the drop-down lists.
-
For information on which API endpoints the XDR Forensics module will connect to, see the XDR Forensics Knowledge Base.
-
For information on which folders and binaries to exclude from endpoint protection solutions, see the XDR Forensics Knowledge Base.
-
If you are installing a deployment that includes XDR Forensics on macOS devices, you will need to grant Full Disk Access permission. See the XDR Forensics Knowledge Base.
Note: Every source of connection will be the Responder, the Responder does not accept any incoming traffic from the internet.
-
-
Click Next.
-
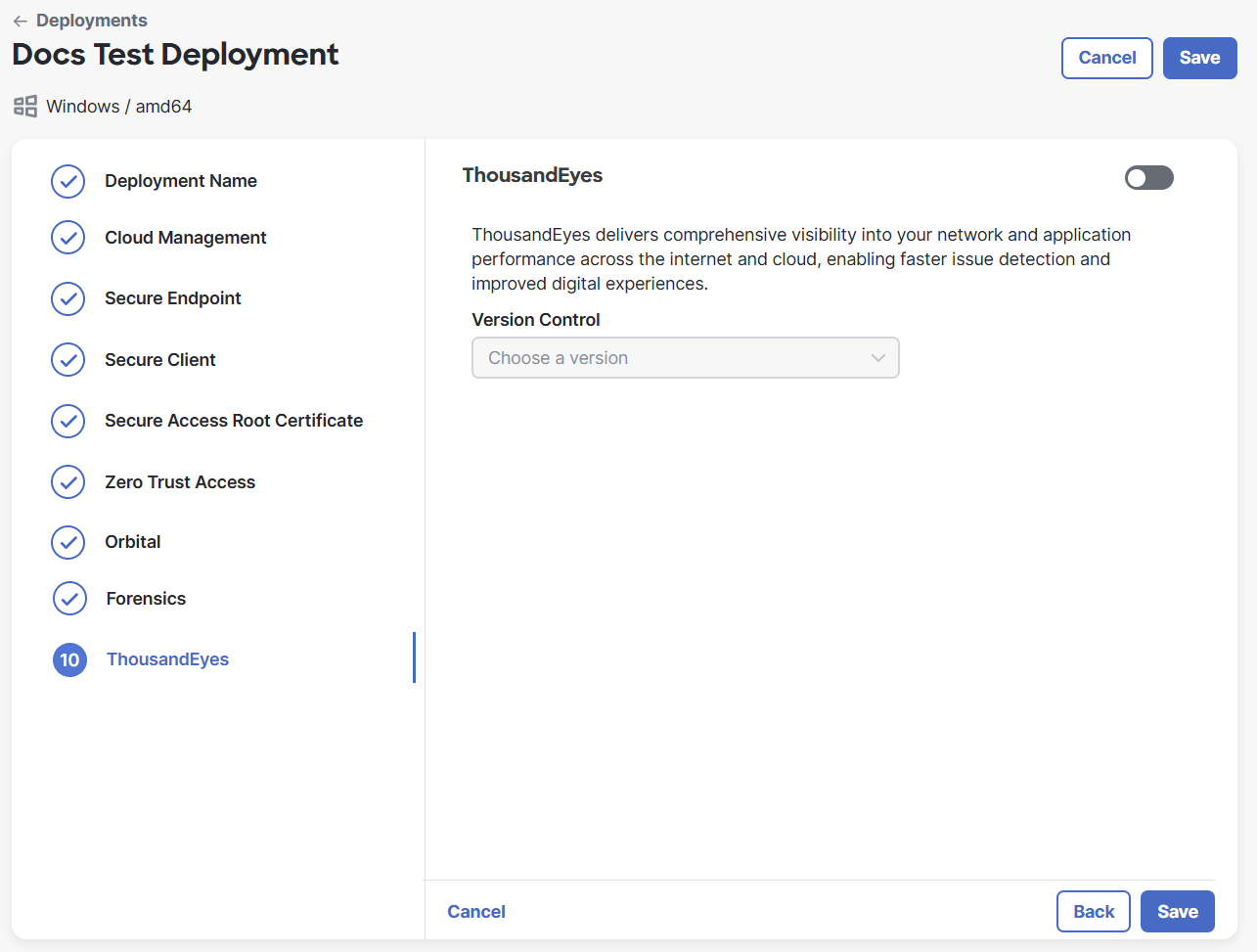
Click the toggle to enable the ThousandEyes module. ThousandEyes delivers comprehensive visibility into your network and application performance across the internet and cloud, enabling faster issue detection and improved digital experiences. If you do not want to include the module, do not click the toggle and proceed to step 29.
-
Choose the version for the ThousandEyes module you want to deploy from the drop-down list.
-
For information on the ThousandEyes Endpoint Agent, see the Endpoint Agents topic in the ThousandEyes documentation.
-
For information on the system requirements, see the System Requirements topic in the ThousandEyes documentation.
-
-
Click Save.
Once you click Save, the Deployment Management page opens, the installers are generated automatically, and you can download a full or network installer. For more information, see the Deployment Management topic.
Note: A maximum of 47 deployments can share the same profile. If you try to create a 48th deployment that uses the same profile, the deployment creation will fail with a notification that the limit was reached. We recommend that you use multiple profiles as needed.
The following table provides a list of supported modules for each operating system, architecture, and minimum Cisco XDR licensing tier:
|
Module |
Minimum Cisco XDR Licensing Tier Required |
Windows |
macOS |
||
|---|---|---|---|---|---|
|
amd64 |
arm64 |
amd64 |
arm64 |
||
|
Cloud Management |
Essential |
Yes |
Yes |
Yes |
Yes |
|
Secure Endpoint |
Essential |
Yes |
Yes |
Yes |
Yes |
|
Secure Client |
Essential |
Yes |
Yes |
Yes |
Yes |
|
Secure Access Root Certificate |
Essential |
Yes |
Yes |
No |
No |
|
Zero Trust Access |
Essential |
Yes |
Yes |
Yes |
Yes |
|
Orbital |
Essential |
Yes |
No |
Yes |
Yes |
|
XDR Forensics |
Advantage |
Yes |
Yes |
Yes |
Yes |
|
ThousandEyes |
Essential |
Yes |
Yes |
Yes |
Yes |