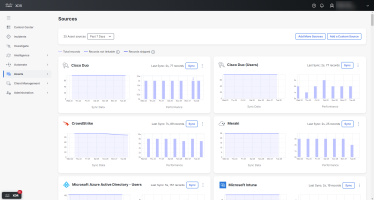
Sources
Note: Only users with an Administrator role can sync, add, and delete sources.
This feature pulls device and user data from the modules you have integrated with Cisco XDR. These data sources can be device managers and security products from Cisco and third-parties.
Choose Assets > Sources in the navigation menu to open the Sources page.
Within each source panel:
- You can click Sync to start a sync job on-demand.
- You can see the status of each source, current sync errors, and the performance history - there’s a drop-down to select the time period being shown.
- Sync Data shows how the number of synchronized objects has changed over time.
- Performance shows how much time it took to synchronize a specific number of records. Hover over the bar to see the details, including the number of records retrieved and the duration of the sync. A taller bar indicates that more records were synchronized over a smaller amount of time.
- If it’s a custom source, you can upload to, update, or remove it.
- Click the
 (Settings) icon in the upper-right corner of the panel to:
(Settings) icon in the upper-right corner of the panel to:
- adjust when and how often Cisco XDR syncs with this source
- register or remove a webhook to this source
Don’t see a source you added? You may need to add your region’s IROH proxy IP addresses to your firewall’s access list in order to allow API connections between your sources and Cisco XDR:
- North America: 35.168.234.165, 35.172.5.95, 34.225.249.84
- European Union: 34.251.83.242, 52.49.85.99, 52.208.164.206
- Asia Pacific, Japan, China: 54.248.49.240, 52.198.165.128, 52.196.126.178
Each source contains information about the devices and users in its own inventory. To update the asset information in its unified inventory, Cisco XDR can use these methods, where supported, to sync with sources:
-
Sync
Pull data on-demand from the source, when you click Sync to manually initiate an update.
-
Full sync
A process that involves a standard API call to the source and download of its full inventory database. This call is performed during an initial sync and later over longer time intervals to avoid exhausting the API subsystem of the source.
-
Delta sync
When possible, the API call returns only what has changed since the last full or delta sync.
-
-
Webhook
Cisco XDR can listen and learn about changes to devices in a source’s inventory by registering with a webhook to the source. In this setup, Cisco XDR connects with the source using a webhook over REST API call and provides the source with a URL. The sources uses this URL to dynamically inform Cisco XDR of a change to a device. In doing so, the API usage will increase accordingly.
To adjust when and how often Cisco XDR syncs with a source, navigate to Assets > Sources and click the ![]() (Open Settings) icon (times are shown in UTC).
(Open Settings) icon (times are shown in UTC).
The following sources support these methods of updating asset information in Cisco XDR:
|
Source |
REST API Full Sync |
REST API Delta Sync |
Webhook |
|---|---|---|---|
|
Cisco Duo |
yes |
yes |
no |
|
Cisco Identity Intelligence |
yes |
no |
no |
|
Cisco Meraki |
yes |
no |
no |
|
Cisco Secure Access |
yes |
yes |
no |
|
Cisco Vulnerability Management |
yes |
no |
no |
|
Crowdstrike Falcon |
yes |
no |
no |
|
custom |
no |
no |
no |
|
Cybereason |
yes |
no |
no |
|
Google Chromebooks |
yes |
no |
no |
|
Google Cloud Platform |
yes |
no |
no |
|
Ivanti Neurons for MDM |
yes |
no |
no |
|
Jamf Pro |
yes |
no |
yes |
|
Microsoft Defender for Endpoint |
yes |
no |
no |
|
Microsoft Defender for Endpoint GCC |
yes |
no |
no |
|
Microsoft Intune |
yes |
no |
no |
|
Omnissa Workspace ONE UEM (formerly VMware Workspace ONE UEM) |
yes |
yes |
no |
|
Orbital |
no |
no |
yes |
|
Palo Alto Networks Cortex XDR |
yes |
no |
no |
|
Secure Client |
yes |
no |
yes |
|
Secure Endpoint (formerly AMP for Endpoints) |
yes |
no |
yes |
|
SentinelOne Singularity |
yes |
no |
no |
|
ServiceNow |
yes |
no |
no |
|
Trend Vision One |
yes |
no |
no |
|
Umbrella |
yes |
yes |
no |
-
Click Add More Sources to go to the Integrations page in Cisco XDR.
-
There are three sections:
- My Integrations
- Cisco Integrations
-
Third-Party Integrations
-
You can search for an integration and filter by its capability, such as show me integrations capable of supporting the Assets feature.
-
Click Get Started or the
 (Add) icon under each integration module and follow the Integration Guide instructions.
(Add) icon under each integration module and follow the Integration Guide instructions.-
Review the important requirements and guidelines in the table below.
-
For additional guidance, see the Integrations help topic.
-
For how to troubleshoot common integration issues, see the TAC Troubleshooting Knowledge Base.
-
Note: There’s an indeterminate amount of time between adding a source and seeing all its assets and their data fully appear in the devices and users table. We aren’t just reflecting the inventory of the source, so you won’t see them all right away. We actually copy the data and examine all the fields to determine if it’s the same asset as another. When we do see the same asset from multiple sources, we process and merge the data to show a single asset and maintain accuracy.
|
Integration Module |
Important Notes |
|---|---|
|
Cisco Duo |
|
|
Cisco Identity Intelligence |
Cisco Identity Intelligence provides user data for the Users page. For more information on how to configure integrations to provide user data, go to the Configuring Integrations topic in the Cisco Identity Intelligence Knowledge Base. |
|
Cisco Meraki |
|
|
Cisco Secure Access |
The Assets feature can pull data from Cisco Secure Access for Windows and Mac devices only; there's currently no support for pulling data from its mobile devices. |
|
Cisco Vulnerability Management |
|
|
Crowdstrike Falcon |
— |
|
Cybereason |
— |
|
Google Chromebooks |
— |
|
Google Cloud Platform |
— |
|
Ivanti Neurons for MDM |
Currently, the Assets feature supports the cloud deployment only; an on-premises deployment has not yet been fully tested. |
|
Jamf Pro |
— |
|
Microsoft Defender for Endpoint |
This source is listed as an application in the Microsoft Cloud Integration on the Integrations page. |
|
Microsoft Defender for Endpoint GCC |
|
|
Microsoft Entra ID (formerly Microsoft Azure Active Directory - Users) |
Note: Cisco XDR user data integration for Entra ID has migrated to Identity Intelligence via Security Cloud Control. |
|
Microsoft Intune |
— |
|
Omnissa Workspace ONE UEM (formerly VMware Workspace ONE UEM) |
|
|
Orbital |
|
|
Palo Alto Networks Cortex XDR |
— |
|
Secure Endpoint (formerly AMP for Endpoints) |
The API key must be Read/Write to successfully register the webhook. However, some environments require keys to be Read/Only for regulatory reasons. In this case, you would still select and create a Read/Write key initially. Then, after the configuration is successful, replace it with a Read/Only key. |
|
SentinelOne Singularity |
— |
|
ServiceNow |
You may want to consider creating a separate ServiceNow user for this integration, as opposed to using your own ServiceNow account. Two-factor authentication is not supported, so ensure that the account you use does not have two-factor authentication enabled. |
|
Trend Vision One |
— |
|
Umbrella |
|
To modify the configuration settings of a source:
- Navigate to Administration > Integrations and expand the My Integrations section.
- Click the integration name to open its current settings.
- Edit the settings as needed, and click Save.
- A message is displayed in the upper portion of the Edit Module form indicating that a health check is running. Once it completes, a message indicates whether there were any issues found with the configuration.
To delete a source:
- Navigate to Administration > Integrations and expand the My Integrations section.
- Click the integration name to open its current settings.
- Click Delete, and then confirm by clicking Delete again.
- The module is removed and its data is no longer available.
Note: You can only import a custom source for devices. User data cannot be imported using a custom source.
To import a particular group of your devices:
-
Click Add a Custom Source.
-
Enter a name and description in the New Custom Source drawer.
-
Click Apply.
-
Find the new custom source card, and click the
 (Open Settings) icon.
(Open Settings) icon. -
Choose Upload CSV File.
-
Click Download Custom Source Template to download our template in a CSV file.
-
Open the downloaded CSV file, and populate the template with your particular group of devices.
Caution: Please follow our template carefully, as importing values entered incorrectly in the CSV file may corrupt your device data in Cisco XDR. Currently, the only fix would be to open a support case with Cisco to have us clear all your device data and start another data sync from scratch.
-
Click Choose File to select a CSV file that has been populated with devices.
Note: The maximum CSV file upload size is 128 MB.
-
Click Upload to add the devices to the custom source.
Note: It takes time to import the data from the sources. You’ll see devices appear as Cisco XDR processes the CSV file you uploaded.
The following table describes the fields in the template and their requirements, where needed.
The CSV headers must match those in our template. Do not modify or delete any headers in the template. However, you can add headers and any column can be empty.
|
Header |
Expected Value |
Notes |
|---|---|---|
|
extId |
The unique identifier of this device from the management system which exported the data. For example, if the system of export is Microsoft Intune, the extId is Intune’s “id” field (such as “id: 9a3eaf6a-9642-41e9-911c-46decfe87424”). |
— |
|
name |
The device’s hostname from the management system which exported the data. |
Do not duplicate hostnames. |
|
osType |
windows, macOS, android, iOS, networkGateway, centos, rhel, ubuntu, oracle, emailSecurityAppliance, webSecurityAppliance, unknown |
— |
|
osVersion |
Example:
|
— |
|
osBuild |
Example: 19042.1466 |
— |
|
hardwareId |
The CPU identifier or serial number of the device. For macOS and iOS, this is the UUID. |
— |
|
macAddresses.0 |
The system accepts up to 2 macAddresses for each device. |
The format should not matter, although aa:bb:cc:dd:ee:ff is preferred. |
|
macAddresses.1 |
— |
— |
|
internalIps.0 |
The system accepts up to 2 internal and external IP addresses for each device. |
Both IPv4 and IPv6 addresses are accepted. |
|
internalIps.1 |
— |
— |
|
externalIps.0 |
— |
— |
|
externalIps.1 |
— |
— |
|
serialNumber |
— |
— |
|
imei |
— |
— |
|
users.0 |
Username (string) for a user from this device. The upload accepts up to 2 users. |
— |
|
users.1 |
— |
— |
|
appUsers.0 |
— |
— |
|
appUsers.1 |
— |
— |
|
emails.0 |
Email addresses of users who sign in with this device. The upload accepts up to 2 email addresses in addition to the “users” and “appUsers” fields. |
Must be in email address format (such as “test-user@securitydemo.net”). |
|
emails.1 |
— |
— |
|
browsers.0.browserFamily |
If the system is an IdP and tracks the device’s browser information. |
Example: Edge Chromium |
|
browsers.0.browserVersion |
— |
Example: 98.0.1108.43 |
|
browsers.0.flashVersion |
— |
Example: uninstalled |
|
browsers.0.javaVersion |
— |
Example: uninstalled |
|
browsers.0.lastUsed |
Date and time when the browser was last used. |
— |
|
browsers.1.browserFamily |
— |
— |
|
browsers.1.browserVersion |
— |
— |
|
browsers.1.flashVersion |
— |
— |
|
browsers.1.javaVersion |
— |
— |
|
browsers.1.lastUsed |
— |
— |
|
created |
Date and time the device first appeared in the management console which exported the data. |
— |
|
lastUpdated |
Date the device record was last updated from the source. |
Must be in numeric format (milliseconds since Unix Epoch). |
|
isCompromised |
A true or false value to indicate if the system has a compromise. |
— |
|
isManaged |
A true or false value to indicate if the system is managed by this company. |
— |
|
labels.0 |
Custom strings that can be used to categorize and filter devices. |
You can add more labels to a device by adding more label columns. For example, labels.1, labels.2, and so on. |
|
value |
The device value can be set from 1-10, where 1 is the least critical and 10 is the most critical. |
The device value will indicate rule assigned if the value is set using a custom source. |
To delete a custom source:
- Find the custom source that you want to delete on the Sources page.
- Click the
 (Open Settings) icon.
(Open Settings) icon. - Choose Delete.
- To confirm removal, click Delete.